What Are the 18 HIPAA Identifiers for PHI?
Whether you’re a healthcare provider, administrator, or medical billing professional, understanding the 18 identifiers of protected health information (PHI) is critical to keeping PHI confidential and secure at all times. This is especially true today when privacy is a luxury that is often difficult to come by. Healthcare information is particularly sensitive and is often susceptible to hacking. So that you know what information you must protect, we take a closer look at the 18 identifiers of PHI and why they matter.
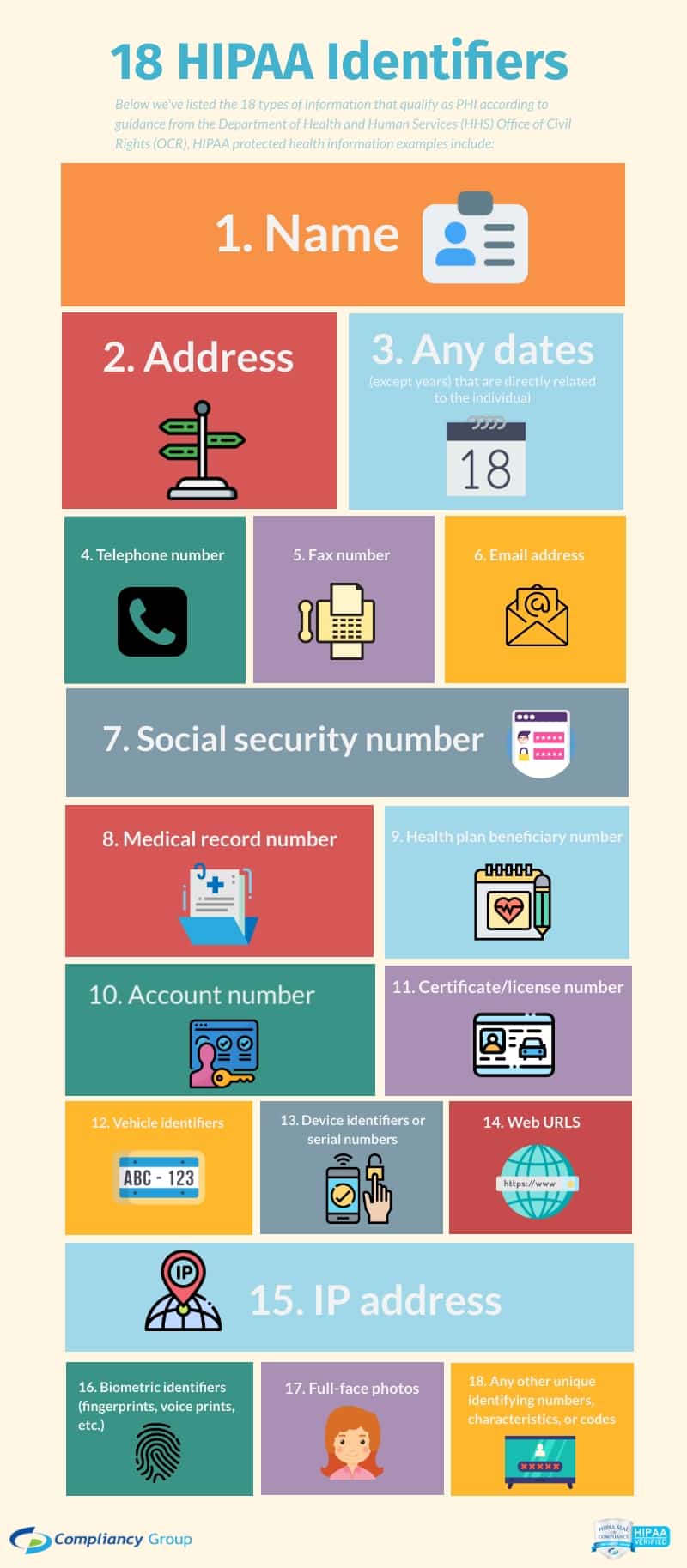
The Department of Health and Human Services (HHS) lists the 18 HIPAA identifiers as follows:
- Patient names
- Geographical elements (such as a street address, city, county, or zip code)
- Dates related to the health or identity of individuals (including birthdates, date of admission, date of discharge, date of death, or exact age of a patient older than 89)
- Telephone numbers
- Fax numbers
- Email addresses
- Social security numbers
- Medical record numbers
- Health insurance beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers
- Device attributes or serial numbers
- Digital identifiers, such as website URLs
- IP addresses
- Biometric elements, including finger, retinal, and voiceprints
- Full face photographic images
- Other identifying numbers or codes
18 HIPAA PHI Identifiers and the HIPAA Privacy Rule
The HIPAA Privacy Rule established standards for the use and disclosure of PHI. The law requires organizations to adopt the “minimum necessary rule” which states that covered entities must take reasonable steps to limit the use and disclosure of PHI. As such CEs must access only the information necessary to accomplish their intended purpose. The HIPAA Privacy Rule also lays out patient rights in regards to their PHI.
- Notice of Privacy Practices (NPP): must be given to patients upon intake. It must be written in a clear manner that patients can easily understand. An NPP describes patient rights in terms of the 18 HIPAA unique identifiers. An NPP also explains what a covered entity (CE) may or may not do with PHI.
- Request Access to Medical Records: patients have the right to request their medical records. Patients must fill out an authorization form to do so.
- Request an Amendment to Medical Records: the HIPAA Privacy Rule mandates that patients have the right to request an amendment of PHI when they believe there has been an error on their record. It is up to the discretion of the covered entity (CE) to determine if the record is accurate.
- Request Special Privacy Protection for PHI: patients have the right to restrict the disclosure of PHI. However, CEs are not required to agree to the request.
- Parents Access to Minor’s Medical Records: in most cases a parent or legal guardian can access a minor’s medical records. The HHS provides examples for situations in which parents cannot access a minor’s medical records.
- The minor consents to care where parental consent is not required
- A court decides that a minor must receive care
- A parent agrees that the minor and covered entity have a confidential relationship
18 HIPAA Identifiers and the HIPAA Security Rule
The HIPAA Security Rule mandates that protected health information (PHI) is secured in the form of administrative, physical, and technical safeguards. As part of the HIPAA Security Rule, organizations must have standards for the confidentiality, integrity, and availability of PHI.
- Confidentiality: PHI may not be disclosed without prior patient authorization
- Integrity: PHI that is transmitted or maintained must only be accessed by those who need access to perform job functions
- Availability: organizations and patients must be able to easily access PHI
Reporting a PHI Breach
While the HHS understands that PHI breaches occur, how you respond to a breach will determine whether or not you face a HIPAA violation as a result. Understanding HIPAA breach notification requirements is crucial to protecting your organization from HIPAA violations and subsequent fines. The HIPAA breach notification rule requires any instance in which the confidentiality, integrity, or availability of protected health information is compromised to be reported.
Common incidents that constitute a PHI breach include:
- Hacking or phishing incidents that allow unauthorized parties to access electronic medical records
- Employees accessing PHI without cause related to their specific job function
- Loss or theft of paper medical records
- Loss or theft electronic medical records (when electronic records are unencrypted), such as those stored on a laptop or USB
- Improper disposal of medical records
All of the incidents listed above must be reported. If an incident compromises the PHI of less than 500 individuals, healthcare organizations have until sixty days from the end of the calendar year (generally March 1st except in a leap year) in which the breach was discovered to report the incident to the HHS Office for Civil Rights (OCR). These smaller incidents should be recorded throughout the calendar year, and can all be reported by this deadline.
When an incident affects 500 or more patients, the breach reporting deadline is much stricter. These larger incidents must be reported within sixty days of discovery, and are posted to the OCR online breach portal for public view. Larger incidents must also be reported to local media.
In either case, patients must be notified no more than sixty days after the incident was discovered via mail. If ten or more patients cannot be contacted by mail, organizations must also post a notice on their website.