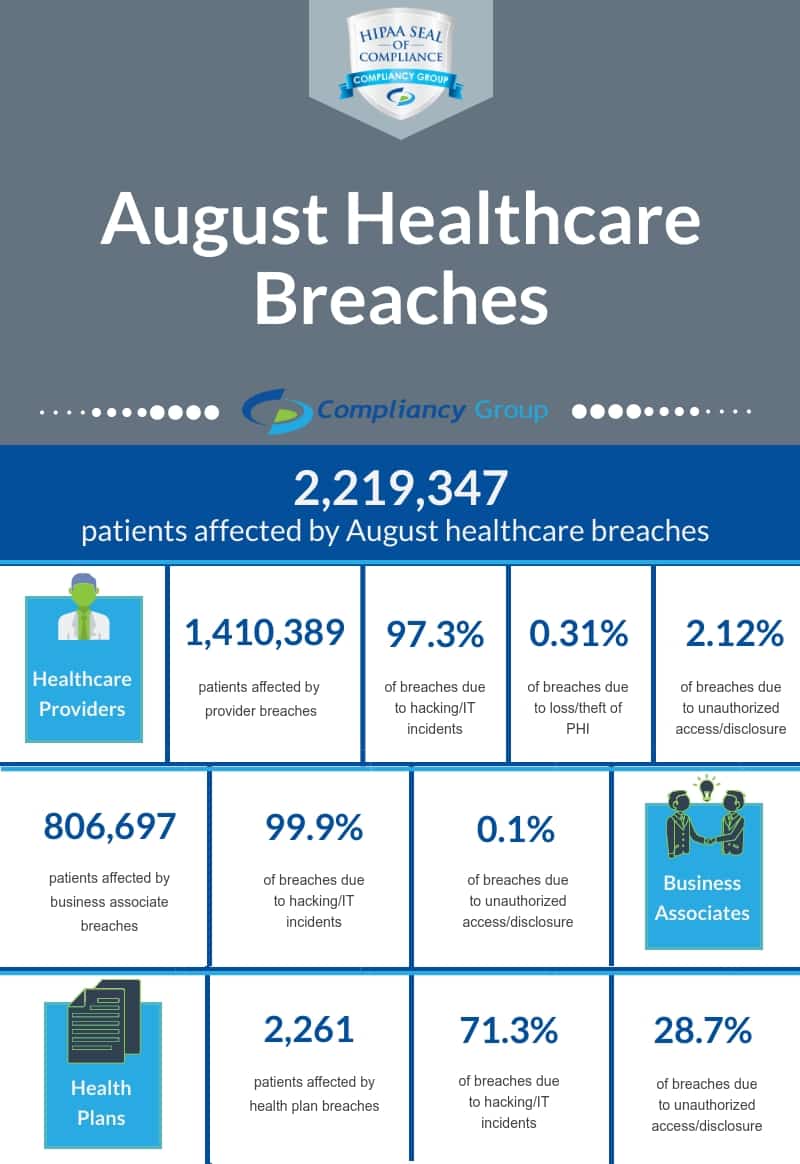
The Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) publicly posts breaches affecting 500 or more patients on their online breach portal known colloquially as the “wall of shame.” In August, 2,219,347 patients were affected by these large-scale breaches (not counting breaches affecting less than 500 patients), with 37 breaches reported. More details on the August healthcare breaches are discussed below.
August Healthcare Breaches: Type of Breached Entity
Healthcare breaches are breaches affecting organizations working with protected health information (PHI). While August healthcare breaches predominantly affected healthcare providers, a significant number of patients were also affected by business associate breaches, and a smaller number of patients by health plan breaches.
August Healthcare Breaches: Hacking/IT Incidents
In the month of August, there were 25 hacking/IT incidents affecting 2,179,781 patients. Hacking/IT incidents continue to be the leading cause behind healthcare breaches, pointing to the need for advanced security measures and employee training. Healthcare hacks often occur due to phishing attacks, which are largely caused by human error.
Phishing attacks occur when hackers email an employee of an organization, impersonating a trusted individual or entity, prompting recipients to click on a malicious link or provide sensitive information, such as login credentials. Hackers then use this to enter an organization’s network, often stealing or maliciously encrypting files, demanding a sum of money for the return of files. This is why employee training is an essential part of preventing healthcare breaches. Employees that are trained to recognize phishing emails, are less likely to fall victim to a phishing attempt.
August Email Hacks Affected 270,760 Patients
◆ OrthoSC, LLC: 3,000 patients affected
◆ Ace American Insurance Company: 8,100 patients affected
◆ Utah Pathology Services, Inc.: 112,124 patients affected
◆ Elwyn: 501 patients affected
◆ HealthFirst Bluegrass: 971 patients affected
◆ Imperium Health LLC: 139,114 patients affected
◆ D&S Residential Holdings, LLC: 2,102 patients affected
◆ The Connection, Inc.: 3,736 patients affected
◆ Comanche County Hospital Authority: 1,112 patients affected
August Network Server Hacks Affected 1,908,520 Patients
◆ Quality of Life Medical and Research Center: 6,000 patients affected
◆ Crozer-Keystone Health System: 6,863 patients affected
◆ Spectrum Health: 52,711 patients affected
◆ Northwestern Memorial HealthCare: 55,983 patients affected
◆ Assured Imaging: 244,813 patients affected
◆ Main Line Health: 60,595 patients affected
◆ Waystar Health: 1,021 patients affected
◆ City of Lafayette Fire Department: 15,000 patients affected
◆ MultiCare Health System: 179,189 patients affected
◆ Saint Luke’s Foundation: 360,212 patients affected
◆ Richard J. Caron Foundation: 22,718 patients affected
◆ University of Florida Health: 135,959 patients affected
◆ Dynasplint Systems, Inc.: 102,800 patients affected
◆ Summit Medical Associates: 7,264 patients affected
◆ Northern Light Health: 657,392 patients affected
Other August Hacks Affected 501 Patients
◆ Humana Inc: 501 patients affected
August Healthcare Breaches: Unauthorized Access/Disclosures
The second most common cause of healthcare breaches in August was unauthorized access/disclosures of PHI, with 8 incidents affecting 31,662 patients. These incidents occur when an unauthorized individual accesses PHI, whether in electronic form, or paper records. In some cases, incidents occur when employees are either designated the wrong level of access to PHI, or an employee or entity shares PHI with another employee or entity that should not have access.
To ensure that employees are aware of the proper uses and disclosures of PHI, it is essential to have policies and procedures dictating when PHI should and should not be accessed or disclosed, and to train employees on your organization’s policies and procedures. In addition, your organization must implement administrative safeguards to ensure adherence to the minimum necessary standard.
August Email Unauthorized Access/Disclosures Affected 12,111 Patients
◆ Washington Department of Social and Health Services: 648 patients affected
◆ Hamilton Health Center, Inc.: 10,393 patients affected
◆ BeneSys, Inc.: 1,070 patients affected
August Paper/Films Unauthorized Access/Disclosures Affected 2,821 Patients
◆ Advocate Aurora Health: 1,907 patients affected
◆ The Iowa Clinic, P.C.: 914 patients affected
August EMR Unauthorized Access/Disclosures Affected 772 Patients
◆ Ashley County Medical Center: 772 patients affected
Other August Unauthorized Access/Disclosures Affected 15,958 Patients
◆ UT Southwestern Medical Center: 15,958 patients affected
August Healthcare Breaches: Loss/Theft
It is understandable that incidents of loss or theft occur. In August, there were 5 incidents of loss/theft affecting 7,904 patients. All of these were the result of a portable electronic device, such as a laptop, with unencrypted protected health information being lost or stolen. When an encrypted device containing PHI is lost or stolen, it is not considered a healthcare breach as the PHI contained on the device cannot be read by unauthorized individuals. This is why it is highly recommended that you encrypt all of your devices that have the potential to access PHI.
August Loss of PHI Affected 3,557 Patients
◆ Cook Children’s Medical Center: 1,768 patients affected
◆ St. Peter’s Health Partners Medical Associates, P.C.: 1,789 patients affected
August Theft of PHI Affected 4,347 Patients
◆ Hoag Clinic: 738 patients affected
◆ BEACON ORTHOPAEDICS & SPORTS MEDICINE: 2,869 patients affected
◆ Consultant Anesthesiologists, Inc.: 740 patients affected









