As working remotely has become the new normal, businesses need to adjust their cybersecurity practices to account for the unique issues remote work poses to security. A recently released report from the Ponemon Institute uncovered the cybersecurity challenges of working remotely, and provided tips for increasing security in a remote environment. The results of the study, as well as tips to increase cybersecurity are discussed.
Cybersecurity Challenges of Working Remotely: Study Results
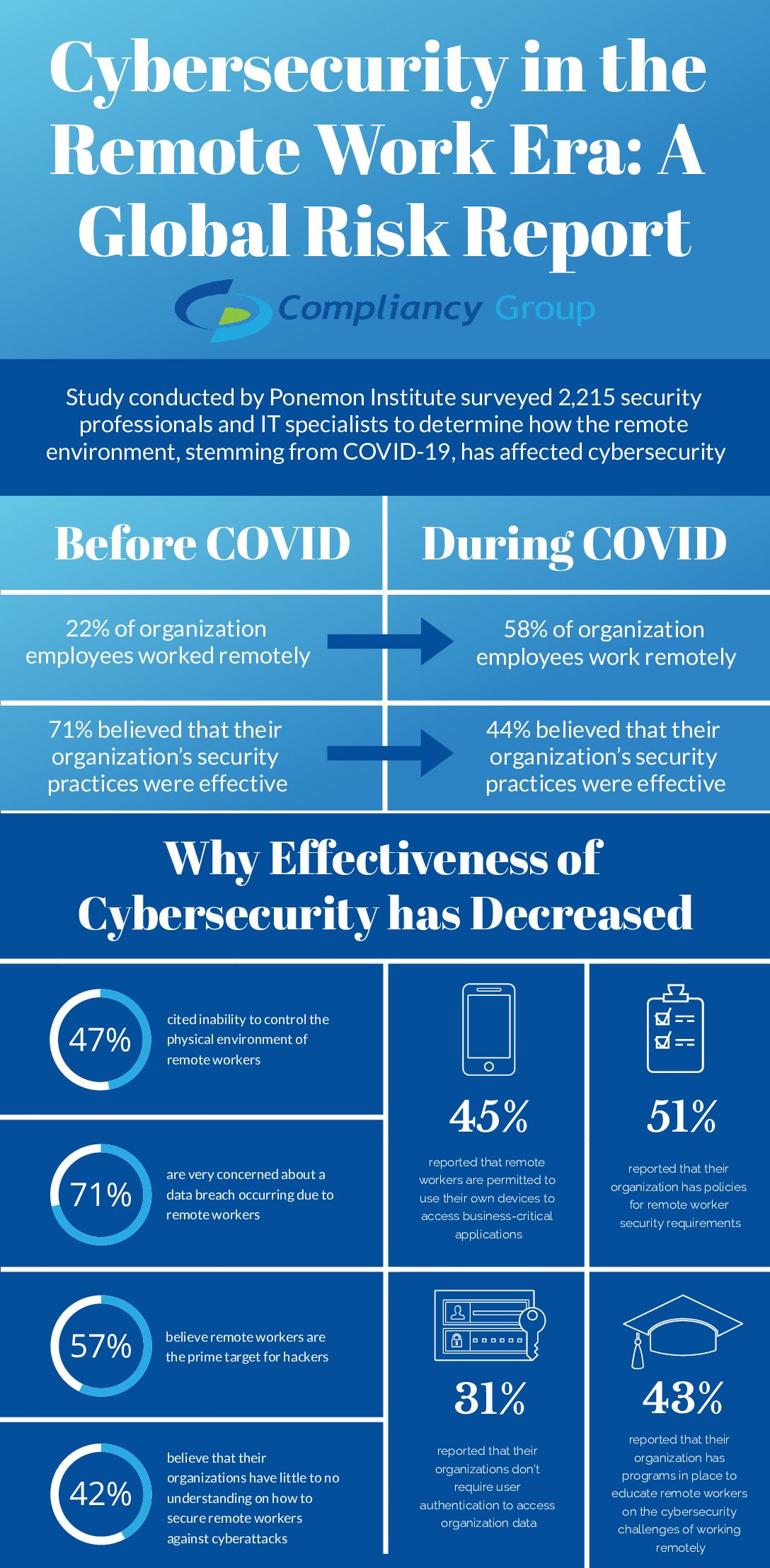
The study conducted by Ponemon Institute, entitled Cybersecurity in the Remote Work Era: A Global Risk Report, surveyed 2,215 security professionals and IT specialists across the United States and Europe to determine how the remote environment stemming from COVID-19 has affected cybersecurity.
Additional Reasons
◈ 56% of respondents believe that the remote environment has significantly reduced their ability to respond quickly to a cybersecurity incident
◈ 59% of respondents reported that their has been a significant increase in access to business-critical applications, with 56% of applications accessed from mobile devices
◈ 69% of respondents that reported that their organization requires user authentication reported that they don’t use multi-factor authentication
◈ 51% of respondents reported that malware got past their organization’s intrusion detection systems, with 49% of respondents reporting that they got past their organization’s anti-virus software
◈ 61% of respondents reported that their organization has experienced a cyberattack
◈ 56% of cyberattacks involved credential theft, while 48% involved phishing/social engineering
◈ 45% of respondents believe their organization’s IT security budget is adequate
◈ 39% of respondents believe that their organization is prepared to manage and mitigate the cybersecurity challenges of working remotely
◈ 53% of respondents reported that their organizations are implementing the necessary security measures to adapt to the remote work environment
◈ 50% of the respondents reported that their organizations are utilizing encryption to protect sensitive data stored on workers’ devices
Cybersecurity Challenges of Working Remotely: Tips to Increase Cybersecurity
To address the cybersecurity challenges of working remotely, it is important to adapt your organization’s security practices.
Policies and Procedures. To increase cybersecurity, your organization should create policies and procedures surrounding the remote work environment. This may include security measures required for remote employees, the use of personal devices to access work materials, and requirements for reporting suspicious activity.
Employee Training. HIPAA already requires organizations to conduct annual training on HIPAA basics and your organization’s policies and procedures. In addition to this training, employees should be trained on how to recognize suspicious activity and phishing emails.
Bring Your Own Device (BYOD). When allowing employees to use their own device (BYOD) to access work materials, it is important that employees enable security features to secure the device from unauthorized access. These measures may include enabling a PIN, fingerprint, or facial recognition to unlock devices.
Multi-factor Authentication (MFA). MFA prevents unauthorized access to data by ensuring that users are who they appear to be. This is enabled by requiring employees to input multiple login credentials to access sensitive data, such as a username and password in combination with security questions, one-time PIN, or biometrics. MFA has become increasingly important with the spike in cyberattacks, preventing hackers with stolen login credentials from accessing data.
Encryption. The best way to secure data is through encryption. Encryption masks sensitive data so that it can only be read with a decryption key.
Access Controls. To limit risk of exposure of sensitive data, and adhere to the HIPAA minimum necessary standard, employees should only be granted access to data that they need to perform their job functions. Through the use of unique login credentials, administrators can designate different levels of access to data based on an employee’s job role.
Audit Logs. Through the use of access controls, access to data can be tracked for each individual employee. By tracking access to data, regular access patterns can be established, allowing quick detection if an unauthorized individual uses an employee’s login credentials to access data.
Software Patches and Updates. To prevent hackers from exploiting weaknesses in software, it is important to keep software updated and implement software patches when they are released.
Password Security. To facilitate security in a work from home environment, employees should be required to change their passwords periodically.
To read more from the Ponemon institute report please click here.










