Does HIPAA Apply to Nonprofit Organizations?

Does HIPAA apply to nonprofit organizations? Many nonprofit organizations wonder whether or not they need to be HIPAA compliant. The answer is simple. If you work with protected health information (PHI) in any capacity, you are required to be HIPAA compliant. HIPAA requires specific measures to be in place, however, the requirements differ depending on the type of nonprofit organization you are. To provide guidance to nonprofit organizations, HIPAA compliance for nonprofits is discussed.
Are You Working with Protected Health Information?
Before we get into specific HIPAA requirements, it is important to understand what protected health information (PHI) is to determine if you are working with PHI. PHI is any piece of information in an individual’s medical record that was created, used, or disclosed during the course of diagnosis or treatment that can be used to personally identify them. This can be related to past, present, or future treatment.
The Department of Health and Human Services (HHS) categorizes PHI into 18 HIPAA identifiers as follows:
- Name
- Address (including subdivisions smaller than state such as street address, city, county, or zip code)
- Any dates (except years) that are directly related to an individual, including birthday, date of admission or discharge, date of death, or the exact age of individuals older than 89
- Telephone number
- Fax number
- Email address
- Social Security number
- Medical record number
- Health plan beneficiary number
- Account number
- Certificate/license number
- Vehicle identifiers, serial numbers, or license plate numbers
- Device identifiers or serial numbers
- Web URLs
- IP address
- Biometric identifiers such as fingerprints or voice prints
- Full-face photos
- Any other unique identifying numbers, characteristics, or codes
What is a Covered Entity?
HIPAA regulation defines covered entities as healthcare providers, health plans, and healthcare clearinghouses involved in the transmission of protected health information. This transmission can take place for the purpose of payment, treatment, operations, billing, or insurance coverage. Covered entities can include organizations, institutions, or persons.
Some examples of covered entities include:
- Community health providers
- Hospitals
- Clinics
- Health insurance providers (including self-insured)
- Nursing homes
What is a Business Associate?
Business Associates are contracted by covered entities to perform a service that may involve the use or disclosure of protected health information. Although they don’t necessarily work with PHI, they may have potential to access it through the services they provide.
Some examples of business associates include:
- Managed service providers
- Software providers
- Third-party claims processors
- Consultants
- Healthcare attorneys
HIPAA for Nonprofit Covered Entities and Business Associates
HIPAA compliance for nonprofit covered entities and business associates differ slightly. This is due to the level of access to PHI the different entities have. For instance, covered entities must comply with the entirety of the HIPAA Privacy Rule, while business associates must only comply with portions of the Rule.
Self-audits.
Healthcare organizations are required to conduct self-audits annually. Covered entities must complete six audits while business associates must complete five.
- IT Risk Analysis Questionnaire: is meant to create a standard device installation and setup process across an entire organization.
- Security Standards: ensures that an organization’s security policies are in line with HIPAA requirements.
- HITECH Subtitle D: ensures that an organization has proper documentation and protocols in relation to Breach Notification.
- Asset and Device: is an itemized inventory of devices that contain ePHI. The device and asset list includes who uses the device and how an organization is protecting the device.
- Physical Site: each physical location must be assessed to determine if there are measures protecting PHI such as locks or alarm systems.
- Privacy Assessment (not required for BAs): assesses an organization’s privacy policies to ensure that PHI is used and disclosed in accordance with HIPAA.
Remediation plans.
By completing your self-audits, gaps in your privacy, security, and breach notification processes are identified. To comply with HIPAA standards, you must create remediation plans to address each of these gaps. Remediation plans should be specific and include timelines for addressing vulnerabilities.
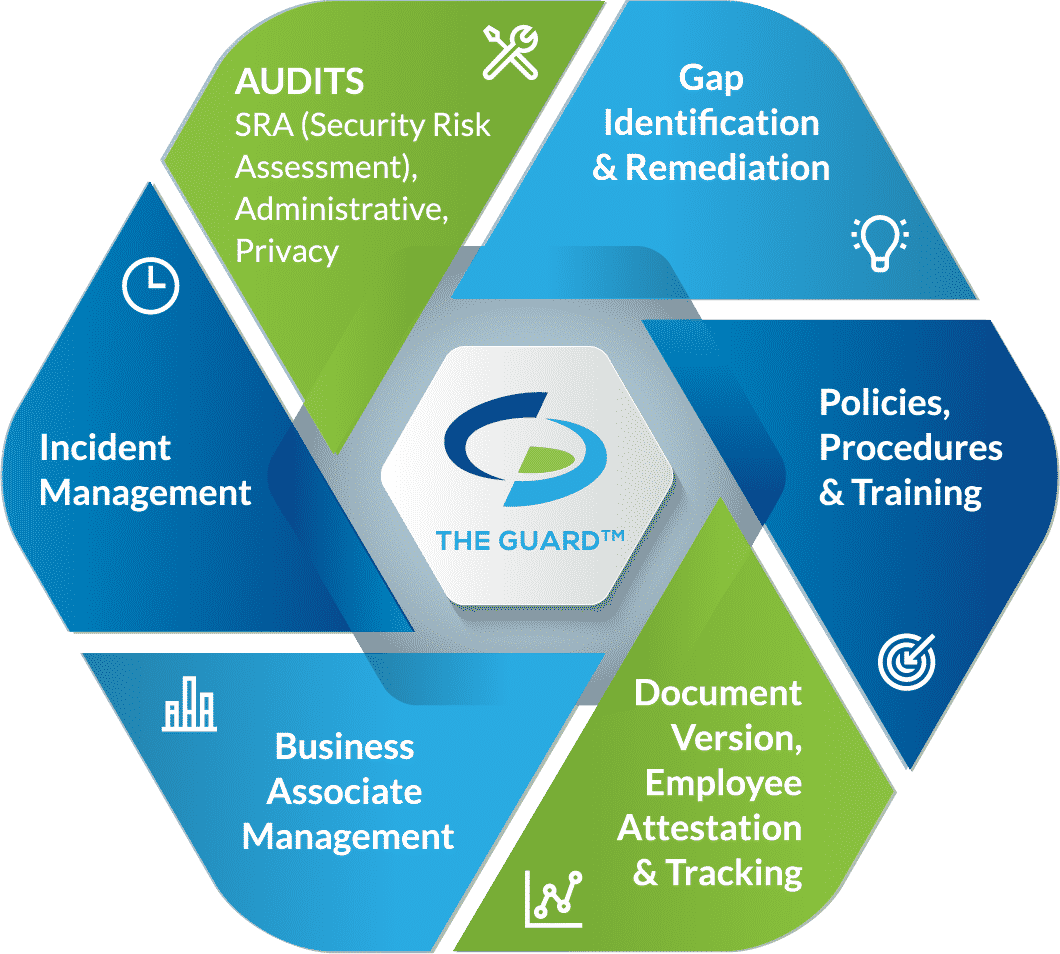
Policies and procedures.
Policies and procedures create guidelines for your organization and staff on the proper uses and disclosures of PHI, how you protect that PHI, and procedures for reporting a breach of PHI. These policies and procedures should be created specifically for your organization to account for any nuances in your business operations. You must review your policies and procedures annually, or whenever there is a change in your business operations, and make amendments when necessary.
Employee training.
To ensure that employees are aware of their HIPAA obligations, they must be trained annually. Training should include HIPAA basics, cybersecurity best practices, and your organization’s policies and procedures. For training to be effective it is important that employees are trained individually, and that they attest that they have read and understood the training material.
Business associate management.
Business associate management is an important part of keeping your organization secure. Covered entities and business associates have an obligation to assess the security of their business associates before doing business with them. This can be done by sending the business associate a vendor questionnaire, similar to what is asked in your self-audits. Additionally, you must have signed business associate agreements (BAAs) with all of your vendors before it is permitted to share PHI with them. A BAA is a legal document that requires each signing party to be HIPAA compliant and maintain their compliance. It also dictates which party is responsible for reporting breach, should one occur.
Incident response.
Any breach compromising the privacy of PHI must be reported to the Department of Health and Human Services and affected patients. For breaches affecting 500 or more patients, the incident must also be reported to local media outlets.







