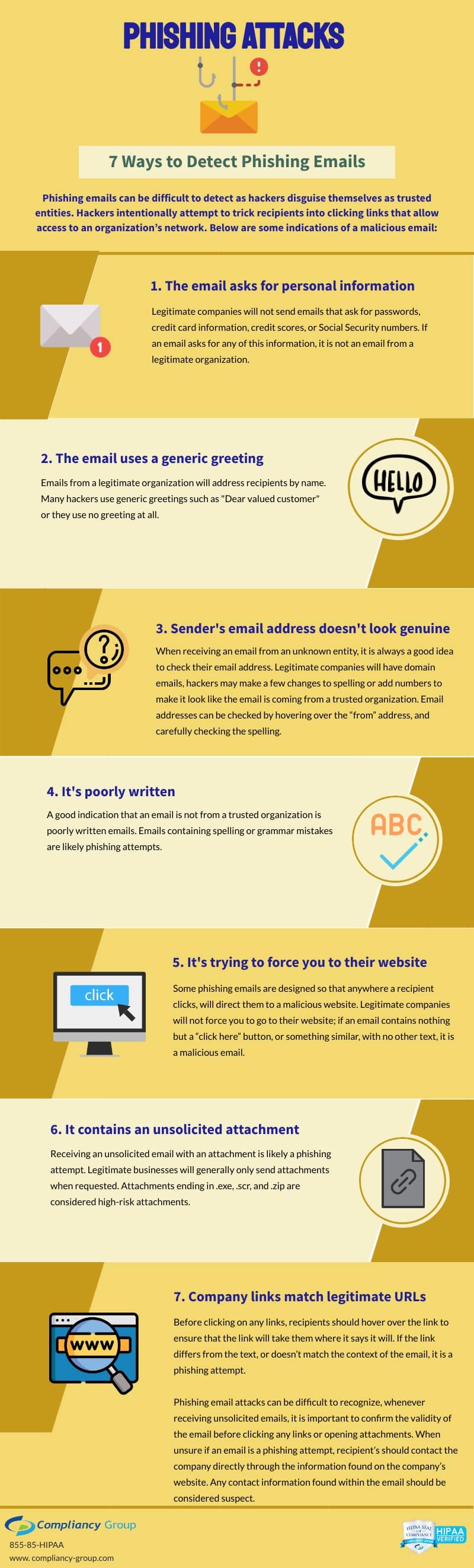
HIPAA Phishing Attacks Affect Millions
HIPAA phishing attacks are increasing in frequency as healthcare organizations are host to a wealth of information. It seems like every day there is news of a phishing attack compromising consumers’ information. Phishing attacks occur when hackers impersonate trusted individuals to gain access to data. Generally, this is done by sending an email, seemingly from a known entity, prompting recipients to click on a malicious link.
Why HIPAA Phishing Occurs
HIPAA phishing can be a huge source of revenue for hackers because it collects and steals data, money, and credentials. Using these tactics hackers target healthcare organizations to gain access to patients’ protected health information (PHI).
PHI is classified into 18 identifiers a follows:
- Patient names
- Geographical elements (such as a street address, city, county, or zip code)
- Dates related to the health or identity of individuals (including birthdates, date of admission, date of discharge, date of death, or exact age of a patient older than 89)
- Telephone numbers
- Fax numbers
- Email addresses
- Social Security numbers
- Medical record numbers
- Health insurance beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers
- Device attributes or serial numbers
- Digital identifiers, such as website URLs
- IP addresses
- Biometric elements, including finger, retinal, and voiceprints
- Full face photographic images
- Other identifying numbers or codes
PHI data is extremely valuable as the information can be used to commit financial fraud or identity theft. Healthcare organizations are often easy targets as they lack advanced security tools. The most vulnerable healthcare organizations are usually small to mid sized businesses as they lack dedicated IT staff.
How to Prevent HIPAA Phishing
There are several options to consider when bolstering cybersecurity.
- Administrative Safeguards: Include creating policies and procedures dictating the proper use and disclosure of PHI. PHI should only be used or disclosed to complete a specific job function, known as the minimum necessary standard. To ensure that this standard is met, employees must be trained annually on their organization’s policies and procedures, as well as HIPAA standards.
- Technical Safeguards: Include securing devices that have access to electronic protected health information (ePHI). ePHI is protected health information in electronic form. Technical safeguards may include encryption, firewalls, antivirus, multi-factor authentication (MFA), etc.
- Self-audits: Healthcare organizations are required to complete six self-audits annually:
- IT Risk Analysis Questionnaire: is meant to create a standard device installation and setup process across an entire organization.
- Security Standards: ensures that an organization’s security policies are in line with HIPAA requirements.
- HITECH Subtitle D: ensures that an organization has proper documentation and protocols in relation to Breach Notification.
- Asset and Device: is an itemized inventory of devices that contain ePHI. The device and asset list includes who uses the device and how an organization is protecting the device.
- Physical Site: each physical location must be assessed to determine if there are measures protecting PHI such as locks or alarm systems.
- Privacy Assessment (not required for BAs): assesses an organization’s privacy policies to ensure that PHI is used and disclosed in accordance with HIPAA.
- Gap Identification and Remediation Plans: Completing self-audits allows organizations to determine where their administrative, physical, and technical safeguards are lacking so they may develop remediation plans to close gaps.
- Policies and Procedures: These must be customized to apply directly to your business practices. Policies and procedures must be reviewed annually to account for any changes in the way you do business. Policies and procedures dictate the proper uses and disclosures of PHI to ensure that your organization and employees are adhering to the minimum necessary standard.
- Business Associate Management: When your business associate is breached, it is likely that your data can also be compromised. This is why covered entities must vet their business associates before working with them. The best way to do this is by sending them a vendor questionnaire. Similar to self-audits, a vendor questionnaire identifies gaps in the business associate’s safeguards so that they may be addressed with remediation efforts. Before working with the vendor, they must agree to implement remediation plans to address identified deficiencies. You must also have a signed business associate agreement (BAA) with each of your business associate vendors. A BAA is a legal document that dictates what protections the business associate is required to have in place. A BAA also mandates that each signing party agrees to be HIPAA compliant, and each party is responsible for maintaining their HIPAA compliance.
- Security Standards: A major component of how to prevent a HIPAA breach is implementing security measures on your devices that “touch” electronic protected health information (ePHI). One “addressable” security measure is encryption. While not specifically mandated by HIPAA, organizations are required to have equally protective measures in place if they do not find encryption feasible for their organization. Encryption masks sensitive data so that it can only be read by authorized individuals possessing a decryption key. Encryption is particularly effective to prevent unauthorized users from accessing devices that are lost or stolen. The best way to prevent a breach due to hackers attempting to access an employee’s computer, or your organization’s network, is through multi-factor authentication (MFA) and employee training. MFA requires users to enter a combination of unique login credentials to access sensitive information. This is generally a username and password in combination with security questions, a one-time PIN, or biometrics.
- Employee Training: Although MFA and encryption ensure that your data is secure, hackers can also access employee’s computers through phishing attempts. Phishing attempts occur when a hacker disguises themselves as a trusted individual, sending employees emails that prompt them to click on a malicious link. Once the link is clicked, hackers can access the employee’s computer, and in some cases, your organization’s entire network. This is why employee training is an important component of how to prevent a HIPAA breach. Employees must also be trained annually on your organization’s policies and procedures, as well as HIPAA standards. This ensures that they understand their obligation to safeguard patients’ PHI.