Learn what an information security policy is, why it matters, and how to write one. Includes ISO/NIST mapping, examples, a checklist, and a free template.

A robust information security policy isn’t just a compliance checkbox, it’s how you set expectations, reduce risk, and satisfy auditors without slowing the business down. For CISOs, IT managers, compliance officers, and security-conscious SMB leaders, a clear, actionable policy ensures your organization can protect sensitive data, meet regulatory expectations, and respond effectively to security incidents.
Authoritative sources, such as the NIST Cybersecurity Resource Center (CSRC), define an information security policy as management’s direction and support for information security across the organization. In practical terms, it sets the rules, responsibilities, and expectations that keep employees, systems, and vendors aligned with your security goals.
This guide will walk you through what an information security policy is, why it matters to your board and regulators, and exactly how to create one. We’ll also map policy sections to ISO 27001 and NIST so you can show evidence during audits plus highlight common pitfalls to avoid. If you’re a CISO, IT or compliance owner at an SMB, or a writer researching for enterprise readers, use this as your practical starting point.
What is an Information Security Policy?
An information security policy is a formal, management-approved document that outlines how an organization protects its information assets. Unlike standards, which define “what” controls are applied, or procedures, which specify “how” to implement them, a policy communicates why security matters, who is responsible, and what behaviors are expected.
Every Information Security Policy should include:
- Management-backed: Leadership approval ensures authority and accountability.
- Clear scope: Defines the systems, data types, and personnel covered.
- Actionable rules: Sets expectations without overloading with technical detail.
- Alignment with frameworks: Maps to ISO 27001, NIST SP 800-53, or CIS controls for regulatory compliance.
By providing this overarching direction, a policy is the foundation upon which standards, procedures, and security awareness programs are built. It’s the compass guiding everyone from the boardroom to the helpdesk.
Why Your Organization Needs One
According to ISMS.online, a clearly articulated policy is the first step toward building an effective Information Security Management System (ISMS).
A comprehensive information security policy is vital for several reasons:
- Regulatory Compliance: Many laws and standards (ISO 27001 Annex A, NIST CSF, HIPAA, GDPR) require a formal information security policy. Without one, organizations risk audits, fines, or loss of business.
- Risk Management: Information security policies communicate expectations around data handling, access control, and incident reporting, reducing operational and reputational risk.
- Operational Consistency: Employees and third parties understand their roles, responsibilities, and limitations, preventing inconsistent practices that can lead to breaches.
- Board Assurance: Leadership can demonstrate due diligence and a proactive approach to protecting sensitive assets.
According to ISMS.online, a clearly articulated policy is the first step toward building an effective Information Security Management System (ISMS).
Core Elements Every Information Security Policy Should Include
A high-quality information security policy typically contains the following sections:
1. Management Statement of Intent & Scope
Every information security policy should begin with a clear declaration from leadership. This statement shows top-level commitment and defines the scope. It specifies which systems, personnel, and data types are covered.
2. Roles & Responsibilities
Without assigned ownership, policies often remain unused. An information security policy must clearly assign responsibilities across all levels:
- CISO/IT security team: policy enforcement, risk monitoring.
- Board/executives: responsible for policy oversight and approval.
- Employees: compliance with acceptable use, reporting incidents, and complete security training.
3. Data Classification & Handling Rules
Organizations should categorize information as Public, Internal, Confidential, or Restricted. Each category has unique handling requirements. For example, Confidential data may require encryption in transit, while Restricted data must be encrypted at rest and protected with stricter access controls. An information security policy template should provide clear rules for storage, sharing, and disposal.
4. Access Control & Acceptable Use
An ISO 27001 information security policy will always include access controls. Accounts must follow the principle of least privilege. Remote work and BYOD arrangements should require secure connections. Acceptable use of devices and internet resources must also be documented.
5. Incident Response & Reporting Obligations
An effective information security policy makes sure that everyone is aware of what to do in the event of a security breach. This includes reporting channels, investigative roles, escalation procedures, and notification of regulators if needed.
6. Vendor and Third-Party Security
Most organizations rely on vendors, contractors, or cloud service providers. An effective information security policy should clearly define expectations for third parties that handle organizational data. This includes:
- Security requirements in contracts
- Data handling and access restrictions
- Right to audit or review third-party security controls
- Regular reassessment of vendor risk
By documenting vendor and supplier obligations in the policy, your organization reduces the chance of security gaps created outside your direct control.
7. Review Cycle & Enforcement
Policies are only effective if they’re enforced. Every information security policy needs to specify disciplinary measures for non-compliance and include a review schedule, such as once a year or after major incidents.
Step-by-Step: How to Write an Information Security Policy
Creating an information security policy is not just writing text, it’s a structured process:
- Stakeholder Interviews: Consult executives, IT, HR, legal, and compliance teams. Each group will have different concerns, and including them early prevents resistance later.
- Define Scope & Objectives: Identify the assets, data flows, and regulatory requirements that the policy should cover. For instance, a healthcare provider will need to include HIPAA compliance, while a financial services company may focus on PCI DSS.
- Align to Standards: Map sections of your information security policy to ISO 27001, NIST CSF, and CIS controls. This makes sure that the document is useful for audits and regulatory reviews.
- Draft the Policy: Keep language simple, authoritative, and actionable. Avoid jargon that non-technical staff will not understand. A good information security template will help you structure each section.
- Review & Approval: Share the draft with senior leadership for feedback and official approval. Without managerial support, the policy will lack authority.
- Communicate & Train: Ensure that every employee understands the policy. Run brief training sessions, provide quick reference guides, and include policy reminders in the onboarding process.
- Publish & Enforce: Place the policy somewhere it can be easily accessed, such as the company intranet. During daily operations, supervisors and managers should remind their teams of the policy requirements.
- Periodic Review: Revisit the policy at least once a year or after a major incident. Update the information security policy to reflect new threats, technologies, or regulations.
Checklist:
Examples & Templates
Starting with a template is one of the best ways to create an information security policy. A template saves time, makes sure no key sections are overlooked, and provides stakeholders with a clear framework to review.
Here’s a simplified ready-to-use information security policy snippet you can adapt:
[Organization Name] Information Security Policy
Effective Date: [DD/MM/YYYY]
Approved By: [CISO / CEO]
- Purpose: To protect the confidentiality, integrity, and availability of organizational information assets.
- Scope: Applies to all employees, contractors, and systems processing organizational data.
- Roles & Responsibilities
-
- CISO: Policy enforcement and risk monitoring.
- Employees: Adherence to acceptable use and incident reporting requirements.
- Data Classification: Public, Internal, Confidential, Restricted, handled per defined guidelines.
- Access Control: Accounts follow least privilege; remote work and BYOD follow secure access protocols.
- Incident Response: All security incidents must be reported to the IT Security Team within 24 hours.
- Review: Policy reviewed annually or after major security events.
For additional reference and authoritative templates:
- SANS Institute: Free Security Policy Templates
- Heimdal Security: Information Security Policy Template Guide
How to Use Templates Effectively
A template should not be copied word-for-word. Consider it a framework instead. Replace placeholders with your organization’s information, remove irrelevant sections, and expand on any areas that require clarification. For example, a small marketing agency may have a short incident response section, while a healthcare provider will need a detailed set of procedures to meet HIPAA requirements.
Common Pitfalls & How to Avoid Them
Despite having good intentions, many organizations create information security policies that appear complete on paper, but fail in practice. Below are the most common mistakes and how to avoid them.
- Too Vague: Avoid generic statements like “protect all data”, as they provide no real guidance. A strong information security policy should specify roles, responsibilities, and procedures.
- Wall of Text: A 40-page document full of legal or technical language would be difficult to read. Break your information security policy into clear sections with bullet points and quick reference checklists.
- No Ownership: The policy becomes ineffective when no one is responsible for enforcement. Assign a CISO, IT manager, or department head for enforcement and incident management.
- Not Mapped to Controls: An information security policy that does not follow ISO 27001 or NIST standards will fail an audit. Include a mapping section that links each part of the policy to specific controls.
- Not Enforced or Reviewed: A static policy is irrelevant. The policy should be reviewed at least once a year or after any major incident. Regular reviews and training sessions ensure that the policy is not just a document on the shelf.
Sources like ScienceDirect emphasize that enforcement, clarity, and alignment are key to policy effectiveness.
Mapping Your Policy to Compliance Frameworks (ISO 27001 / NIST / CIS)
Creating an information security policy is only the first step. To make it effective during audits and assessments, you need to demonstrate how it complies with established frameworks like ISO 27001, NIST, and CIS controls. Aligning your policy to these guidelines provides evidence of compliance and makes sure nothing crucial is overlooked.
Here’s a simple example of how a policy section can align with ISO 27001 clauses and NIST Controls:
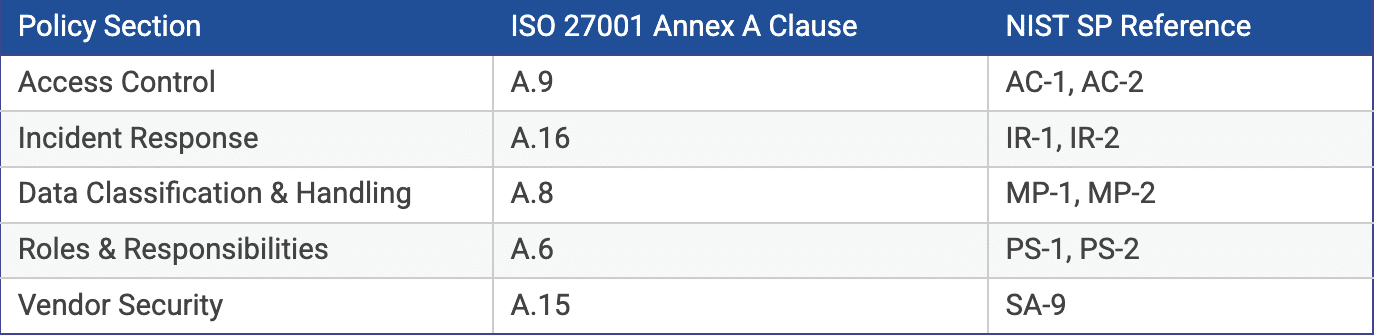
Mapping policies ensures you meet regulatory audits and framework expectations efficiently. ISMS.online and NIST CSRC provide detailed guidance for alignment.
FAQs
Q: How often should an information security policy be reviewed?
A: At least annually or after major incidents, technology changes, or regulatory updates.
Q: Does ISO 27001 require a policy?
A: Yes. ISO 27001 Annex A requires a formal management-approved policy as part of an ISMS.
Q: Policy vs Standard vs Procedure: what’s the difference?
A: Policy sets “what” and “why,” standards define “what must be done,” and procedures explain “how to do it.”
Q: Who is responsible for maintaining an information security policy?
A: The Chief Information Security Officer (CISO) or equivalent role is usually responsible. However, executives, managers, and employees all share responsibility for following and enforcing the policy.
Next Steps
Implementing an effective information security policy is the foundation of a strong security program. Once your policy has been created, the next step is to execute: train your team, review it regularly, and align it to the frameworks your auditors require.
To help you get started, we have created a free, ready-to-use information security policy template. It includes the core sections, checklists, and compliance mapping so you can adapt it quickly to your organization.
With a solid policy in place and proper execution, your organization will be better prepared to protect data, satisfy regulators, and successfully address security threats.









