Ensuring the security and privacy of sensitive information in today’s digital age is extremely important and must be taken seriously. Organizations must adopt robust measures to protect their customers’ data from unauthorized access or breaches. SOC 2 compliance has emerged as a widely recognized framework that organizations can adhere to to demonstrate their commitment to data security. Let’s get into the SOC 2 compliance checklist and provide valuable insights into its significance.
Understanding SOC 2 Compliance: Cracking the Code
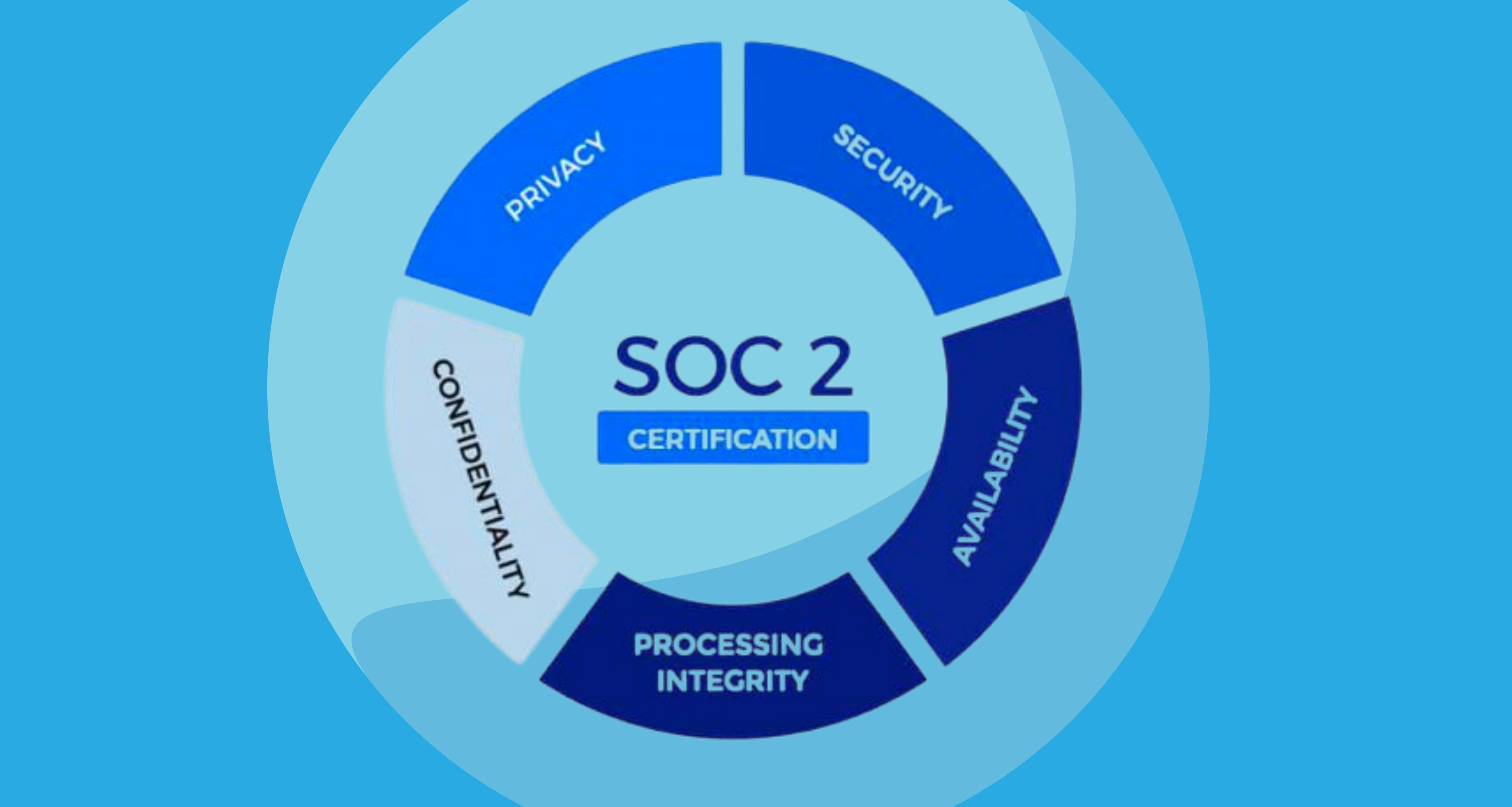
SOC 2 compliance is an auditing procedure developed by the American Institute of Certified Public Accountants (AICPA). It focuses on five key trust service criteria:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Achieving SOC 2 compliance ensures that an organization has implemented adequate controls and safeguards to protect patient data.
The Ultimate SOC 2 Compliance Checklist Template: Your Pathway to Security
To ensure the security, availability, processing integrity, confidentiality, and privacy of data within an organization, it is essential to adhere to the SOC 2 framework.
1. Establishing Security Policies & Procedures
One crucial aspect of the SOC 2 compliance checklist is creating comprehensive security policies and procedures. These documents outline how an organization handles information security risks including:
- Physical Access Controls
- Logical Access Controls
- System Monitoring
- Incident Response Plans
- Employee Training Programs
2. Conducting Regular Risk Assessments
Organizations seeking SOC 2 compliance should regularly conduct risk assessments to identify potential vulnerabilities in their systems and processes. This involves:
- Evaluating Threats
- Analyzing Impacts of Threats
- Implementing Appropriate Controls to Mitigate Risks
3. Implementing Access Controls
Access controls play a vital role in the SOC 2 compliance checklist by protecting sensitive information from unauthorized access or disclosure. Organizations need to implement stringent access control mechanisms, such as:
- Multi-Factor Authentication
- Role-Based Access Controls
- Least Privilege Principles
- Regular User Access Reviews
4. Ensuring Data Privacy
Data privacy is another critical component of the SOC 2 compliance checklist. Organizations must establish protocols when it comes to:
- Collecting
- Storing
- Transmitting
- Deleting
5. Monitoring & Logging
Continuous monitoring and logging of systems and networks are essential for promptly detecting and responding to security incidents. Organizations should implement robust logging mechanisms to:
- Track User Activities
- Monitor System Performance
- Detect Anomalies
- Investigate Potential Security Breaches
6. Incident Response Planning
Having a well-defined incident response plan is crucial in today’s threat landscape. SOC 2 compliance requires organizations to establish protocols for:
- Identifying
- Analyzing
- Containing
- Eradicating
- Recovering
Implementing all these actions in times of security incidents is crucial. Regular testing and updating of these plans are also necessary to ensure their effectiveness.
7. Vendor Management Controls
Organizations often rely on third-party vendors for various services. The SOC 2 compliance checklist template necessitates the implementation of vendor management controls to ensure that these partners adhere to similar security standards. This includes:
- Conducting Due Diligence Assessments
- Establishing Contractual Obligations for Data Protection
- Regularly Monitoring Vendor Performance
8. Conducting Employee Training Programs
Employees play a significant role in maintaining information security. Implementing comprehensive training programs ensures that employees are aware of their responsibilities regarding:
- Data Protection
- Privacy Regulations
- Social Engineering Threats
- Best Practices for Safeguarding Information
Overall, achieving SOC 2 readiness and following the guidelines outlined by the SOC 2 compliance checklist template demonstrates an organization’s commitment to complete security and privacy of patient data. By continuing to abide by the SOC 2 compliance checklist, organizations can establish robust controls and safeguards that protect sensitive information. Prioritizing data security enhances customer trust and helps organizations stay ahead of the curve in an increasingly competitive digital environment.










