The influx of third-party breaches should be of concern for any organization working in healthcare. Hackers often target third-party providers to access the sensitive data that they manage for their clients. This fact is evident by the recently announced Kroger pharmacy breach which stemmed from a vulnerability in their file transfer provider, Accellion. More details about the Kroger pharmacy breach are discussed.
What We Know About the Accellion Breach
In December 2020, it was reported that ransomware gangs “Clop” and “FIN11” targeted approximately 100 companies using vulnerabilities found in Acellion’s File Transfer Appliance. Once the gangs had access to the companies’ files, they issued ransom notes in the form of threatening emails that claimed the groups would release sensitive information publicly if the companies declined to pay the ransom.
According to BleepingComputer, the following is the ransom email that the companies received:
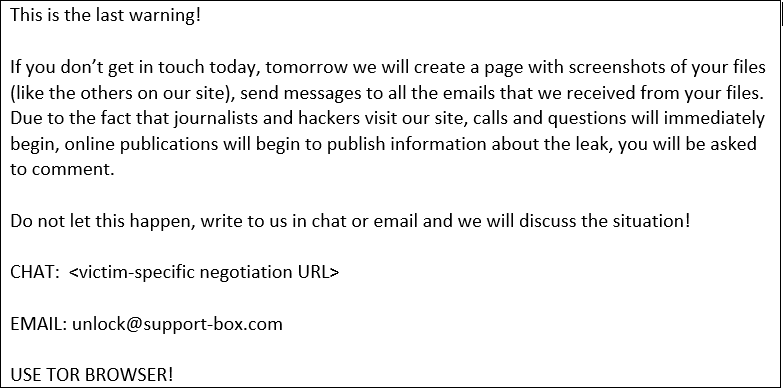
BleepingComputer, who has been tracking the incident, found that in addition to Kroger, several other major companies were targeted including QIMR Berghofer Medical Research Institute, Singtel, the Australian Securities and Investments Commission, Reserve Bank of New Zealand, ABS Group, Jones Day, Danaher, Fugro, the University of Colorado, and the Office of the Washington State Auditor.
To prevent a similar incident from occurring in the future, Accellion has released a patch to address known vulnerabilities, and are encouraging clients to upgrade to kiteworks. “Our latest release of FTA has addressed all known vulnerabilities at this time,” commented Frank Balonis, Accellion’s Chief Information Security Officer. “Future exploits, however, are a constant threat. We have encouraged all FTA customers to migrate to kiteworks for the last three years and have accelerated our FTA end-of-life plans in light of these attacks. We remain committed to assisting our FTA customers, but strongly urge them to migrate to kiteworks as soon as possible.”
In the past, other companies such as Microsoft have warned their customers against using legacy software that are usually vulnerable to hacks. When software providers release new versions of their product, they generally stop supporting the old software with patches, so any known vulnerabilities are left vulnerable. This is why it is essential to upgrade software when new versions become available.
Kroger Pharmacy Breach Details
As investigations into the Kroger pharmacy breach are ongoing, it is unclear how many patients were potentially affected by the incident. However, Kroger stated that the breach affected beneficiaries under its Health and Welfare Benefit Plan and Retiree Health and Welfare Benefit Plan. Kroger is contacting patients affected by the breach and will be providing them with one year of complementary credit monitoring. Protected health information (PHI) potentially compromised in the incident included patient names, dates of birth, Social Security numbers, phone numbers, email addresses, home addresses, insurance claim information, and prescription information.
The breach may have also affected affiliated pharmacies including Jay C Food Stores, Dillon Companies, Baker’s, City Market, Gerbes, King Soopers, Quality Food Centers, Roundy’s Supermarkets, Copps Food Center, Mariano’s Metro Market, Pick N Save, Harris Teeter, Smith’s Food and Drug, Fry’s Food Stores, Healthy Options, Postal Prescription Services and Kroger Specialty Pharmacy Holdings.
Since the breach, Kroger has ceased business with Accellion.









