What is a Risk Assessment Tool?
A risk assessment tool is a service that is used to assess an organization’s level of risk. In the healthcare HIPAA context, the risk assessment tool that is most commonly used is known as a security risk assessment tool. Under the HIPAA Security Rule’s security management process, covered entities and business associates must implement policies and procedures to prevent, detect, contain, and correct security violations. Organizations must implement the security process by performing a risk assessment, risk management, by developing a sanction policy, and by performing information system activity review. Performance of the first of these tasks, performing the risk assessment, can be aided by use of a risk assessment tool. The risk assessment tool is discussed below.
What is a Risk Assessment Tool? Features of a Risk Assessment Tool
A risk assessment tool allows a user to input data necessary to conduct a risk analysis. A risk analysis consists of six elements:
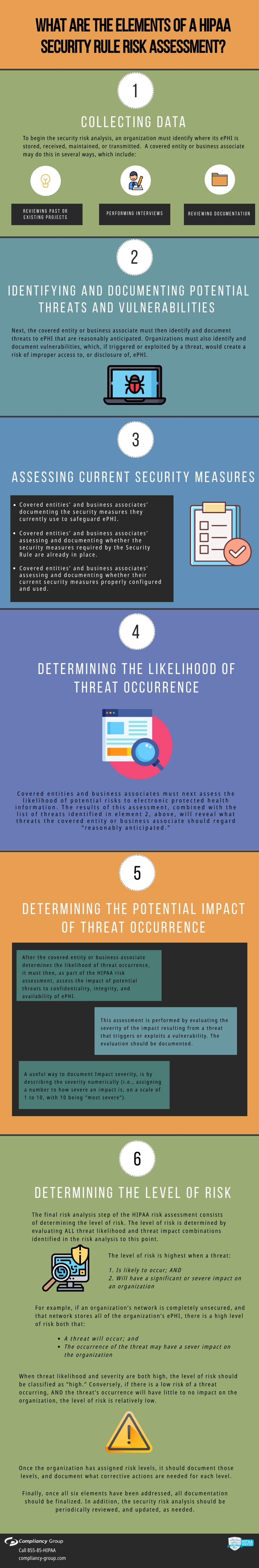
Element 1: Collecting Data
To begin the security risk analysis, an organization must identify where its ePHI is stored, received, maintained, or transmitted. It can do this in several ways, by:
◈ Reviewing past or existing projects
◈ Performing interviews
◈ Reviewing documentation
The data gathered on the ePHI during data collection must be documented.The risk assessment tool is an online tool allowing a user to input ePHI, and to sort and classify that ePHI depending upon how it is stored, maintained, received, or transmitted.
Element 2: Identifying and Documenting Potential Threats and Vulnerabilities
Next, an organization must identify and document reasonably anticipated threats to ePHI. Organizations must also identify and document those vulnerabilities which, if triggered or exploited by a threat, would create a risk of improper access to, or unauthorized disclosure of, ePHI. The risk assessment tool allows the user to input the various types of threats. The user inputs the threats by category (i.e., technical threats, natural threats, human threats, environmental threats). While identifying potential threats, covered entities must also identify and document vulnerabilities which, if triggered or exploited by a threat, would create a risk to ePHI. The risk assessment tool allows the user to input system vulnerabilities associated with a given threat. The threat-vulnerability relationship is simple: a vulnerability is a technical problem that needs to be corrected. An example of a vulnerability is not having access controls. Failure to have access controls can be exploited by endpoint threats such as malware, exploits and fileless attacks. If the vulnerability were exploited by the threat, unauthorized individuals could access ePHI.
Element 3: Assessing Current Security Measures
For this part of the security risk analysis, organizations should address their “state of security.” They should do so by assessing and documenting
◈ The security measures they use to safeguard ePHI;
◈ Whether security measures required by the Security Rule are already in place;. and
◈ Whether current security measures are configured and used properly.
The risk assessment tool can contain a series of questions, tied to the HIPAA Security Rule requirements. For each question, a user can answer “yes” if a required Security Rule measure is in place, and “no” if it is not. If a measure is in place, but is not configured or used properly, the user can note this in the “comments” box to the right of the answer to a given question on the risk assessment tool.
Element 4: Determining the Likelihood of Threat Occurrence
Organizations must then assess the likelihood of potential risks to ePHI. The results of this assessment, combined with the list of threats identified in element 2, will reveal what threats should be regarded as “reasonably anticipated.”
“The likelihood of threat occurrence,” as that term relates to the HIPAA Security Rule, is the probability that a threat will trigger or exploit a specific vulnerability.
Covered entities should consider each potential threat and vulnerability combination (as a reminder, Identification and Documentation of Potential Threats and Vulnerabilities is step 2 of the security risk analysis) and rate them by likelihood (or probability) that the combination would occur.
Ratings such as high, medium, and low, or numeric representations of probability (i.e., a scale of 1 to 10, with one being “very unlikely” and 10 being “extremely likely”) may be used to express the likelihood of occurrence. A rating of “10” indicates that a high probability exists that a threat will trigger or exploit one or more vulnerabilities. A rating of “1” indicates that a low probability exists that a threat will trigger or exploit a single vulnerability. The low probability can be attributed to, for example, the existence of one, single organizational deficiency or inadequate security measure, such as improper configuration of security controls.
Using the online risk assessment tool, the user can analyze each threat and vulnerability combination, and then input the threat occurrence likelihood into the tool.
Compliancy Group’s Risk Assessment Tool
Compliancy Group’s risk assessment tool offers clients a guided analysis of their current security practices. Our Compliance Coaches™ walk clients through creating an IT asset inventory and completing a risk assessment, so that gaps in safeguards can be identified. Find out more about our guided risk assessment tool!
Element 5: Determining the Potential Impact of Threat Occurrence
After an organization determines the likelihood of threat occurrence, it must assess the impact of potential threats to confidentiality, integrity, and availability of ePHI. This can be done by assessing the severity of the impact resulting from a threat that triggers or exploits a vulnerability. The assessment should be documented. The risk assessment tool contains space for the documentation to be inputted. Impact severity can be described numerically. A number of “1” can be inputted into the risk assessment tool to describe an impact with low severity. A number of ten can be used to document an impact with high severity.
Element 6: Determining the Level of Risk
The level of risk is determined by evaluating ALL threat likelihood and threat impact combinations identified in the risk analysis so far.
The level of risk is highest when a threat 1) is likely to occur; AND 2) will have a significant or severe impact on an organization. For example, if a network is completely unsecured, and that network stores all of the organization’s ePHI, two things are likely to happen: A threat will occur, and its occurrence may have a severe impact on the organization. When threat likelihood and severity are both high, the level of risk should be classified as “high.”
On the other hand, if there is a low risk of a threat occurring, AND the threat’s occurrence will have little to no impact on the organization, the level of risk is relatively low.
Once the organization has assigned risk levels, it should document those levels, and document what corrective actions are needed. The risk assessment tool can assist a user in each step of this process. Through the risk assessment tool, a user can input risk levels (i.e., “high,” “medium”), and can then add notes as to what corrective action, or risk management, is needed.






