What is an Effective Compliance Program
The Health Insurance Portability and Accountability Act (HIPAA) enacted in 1996 established industry standards for healthcare organizations as well as vendors with healthcare clients. HIPAA law mandates the secure handling of protected health information (PHI) in the form of administrative, physical, and technical safeguards. PHI is any individually identifiable health information such as name, date of birth, treatment information, financial information, etc. An effective compliance program covers every aspect of HIPAA regulation.
Any organization working in healthcare has the responsibility to be HIPAA compliant, this includes covered entities (CEs) as well as business associates (BAs). A covered entity is anyone directly involved in the treatment, payment, or operations of a patient. A business associate is contracted by a CE for a service, but does not work directly with PHI.
An effective compliance program addresses:
- Audits: HIPAA law requires organizations to conduct self-audits to determine if their security practices are adequately protecting PHI. Covered entities are required to perform six audits, while business associates must conduct five. All audits must be completed annually to maintain an effective HIPAA compliance program.
The required audits are as follows:
-
- IT Risk Analysis Questionnaire: is meant to create a standard device installation and setup process across an entire organization.
-
- Security Standards: ensures that an organization’s security policies are in line with HIPAA requirements.
-
- HITECH Subtitle D: ensures that an organization has proper documentation and protocols in relation to Breach Notification.
-
- Asset and Device: is an itemized inventory of devices that contain ePHI. The device and asset list includes who uses the device and how an organization is protecting the device.
-
- Physical Site: each physical location must be assessed to determine if there are measures protecting PHI such as locks or alarm systems.
-
- Privacy Assessment (not required for BAs): assesses an organization’s privacy policies to ensure that PHI is used and disclosed in accordance with HIPAA.
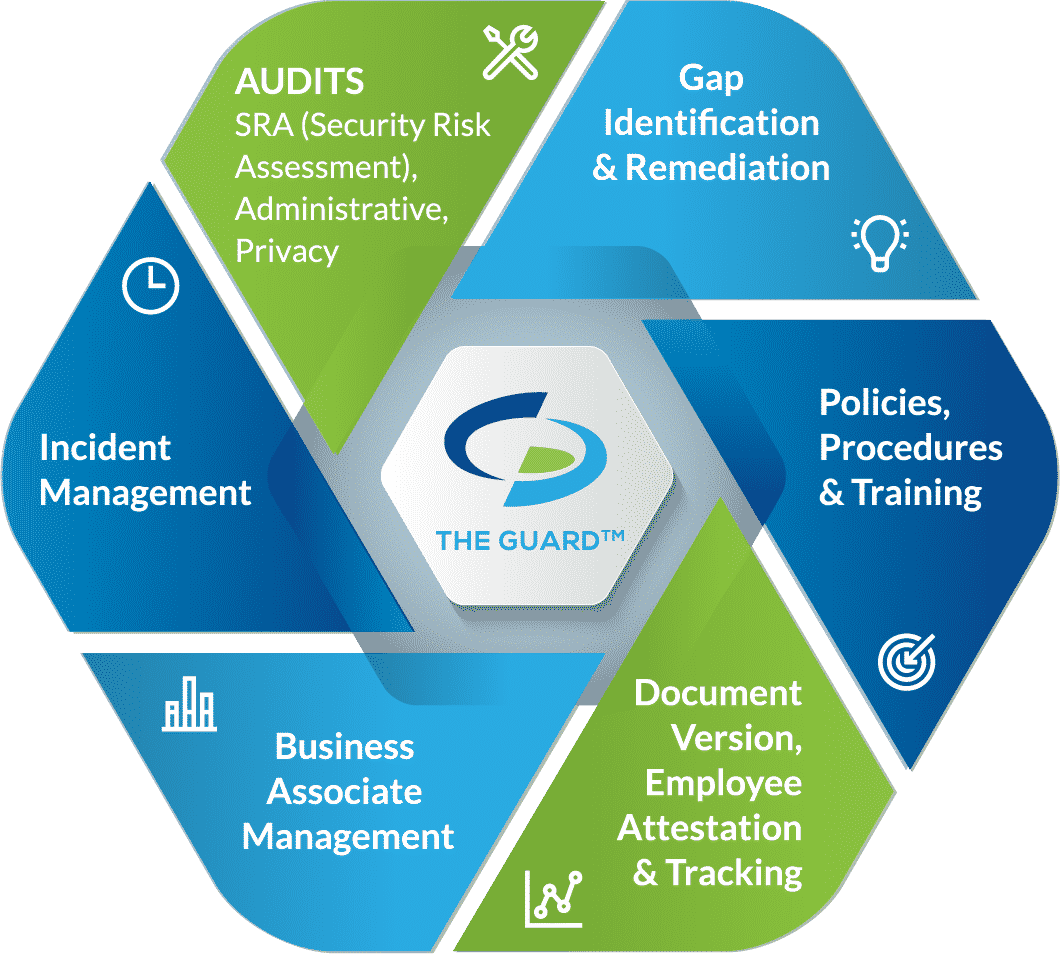
- Gap identification and remediation: completing self-audits allows organizations to determine their gaps in protecting PHI. A remediation plan is meant to address those gaps by creating a plan to fix issues. Remediation plans must be documented, including dates in which remediation efforts will be implemented.
- Policies, procedures, and training: policies and procedures must be created for an organization’s specific needs. An old or bought employee manual will not suffice when it comes to HIPAA compliance. An effective compliance program includes policies and procedures created for a specific organization. In addition, they must be updated regularly to fit an organization’s current operating model.
- Employee attestation and tracking: an organization is not HIPAA compliant if they don’t document their efforts. Organization’s must have a way to prove that employees have gone through HIPAA training. Employee attestation is when an employee reads through an organization’s policies, procedures, and training material and legally confirms that they have read and understood all of the materials.
- Business associate management: organizations working in healthcare must vet their vendors and secure business associate agreements (BAAs). A BAA must be executed before PHI can be shared between the parties. A BAA also ensures that each party is HIPAA compliant. A BAA limits the liability for both parties involved as it says that parties are accountable for themselves, meaning that in the event of a breach, only the responsible party will be held accountable. However, organizations that don’t properly vet their vendors will also be held accountable if a breach occurs. BAAs must be reviewed annually to incorporate any changes in the nature of an organization’s relationship with the vendor.
- Incident management: in the event of a data breach, healthcare organizations and the vendors that service them are required to report the incident. The HIPAA Breach Notification Rule requires organizations to report breaches to the Department of Health and Human Services (HHS) as well as affected individuals. In the case of a Meaningful Breach, affecting more than 500 individuals, organizations must also report the incident to the media. Organizations are required to report the incident within 60 days of discovering the incident. When organizations experience a Minor Breach, affecting less than 500 individuals, they have until the end of the calendar year to report the incident; they don’t need to report the incident to the media.






