Is Your Software HIPAA Compliant?
HIPAA Software Development
When your software is used by healthcare organizations to create, maintain, store, transmit, or receive protected health information, your software must be HIPAA compliant. HIPAA compliant software has certain security controls in place to protect the sensitive health information. As such, when developing your software, you must keep in mind how your software will keep patient information private and secure. Read more about HIPAA software development below.
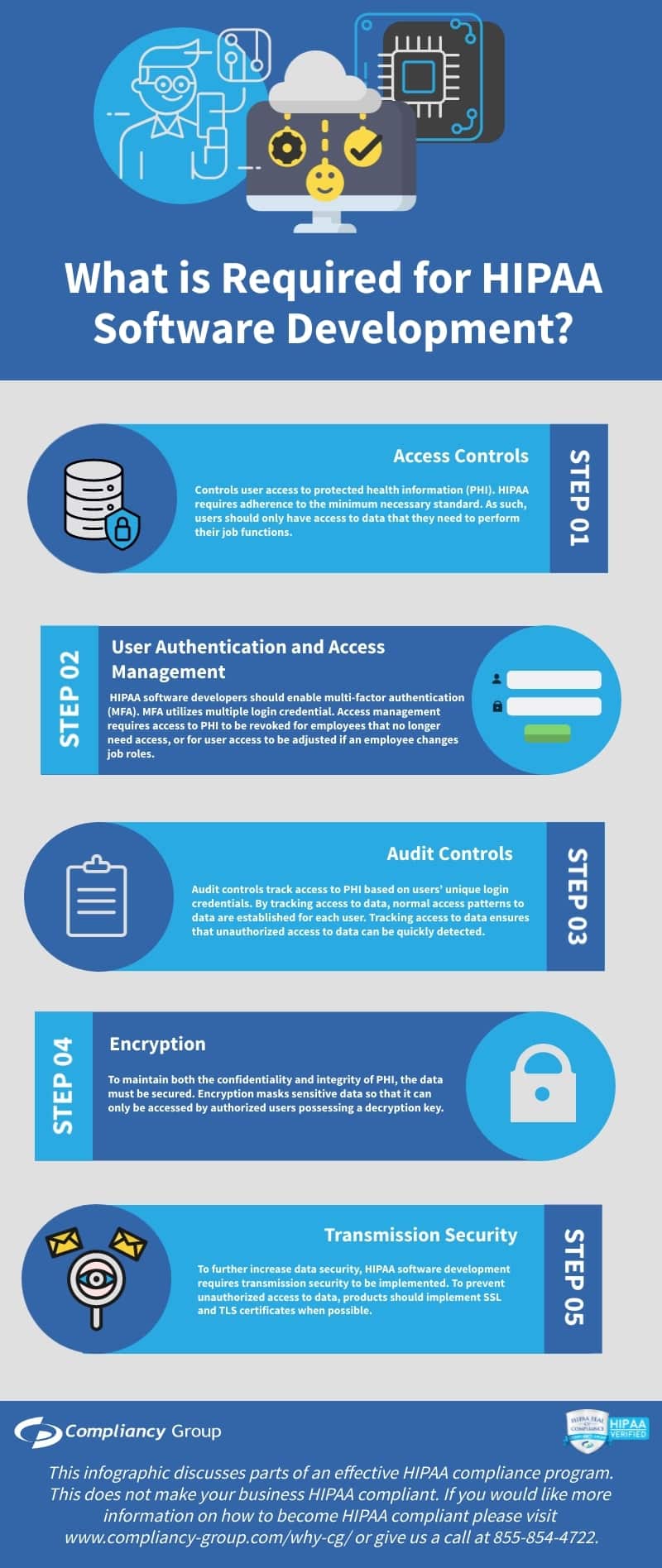
What is Required for HIPAA Software Development?
When developing software for the healthcare industry, there are several security factors that must be considered for HIPAA software development.
HIPAA software development security features include:
1. Access Controls
2. User Authentication and Access Management
3. Audit Controls
4. Encryption
5. Transmission Security
Access Controls.
Controls user access to protected health information (PHI). HIPAA requires adherence to the minimum necessary standard. As such, users should only have access to data that they need to perform their job functions.
Access controls include:
◈ Unique Login Credentials. Each employee must have unique login credentials for accessing data. Unique login credentials enable role-based access, user authentication and access management, and audit controls.
◈ Role-based Access. Employees must be designated different levels of access to data based on their job functions. Role-based access ensures adherence to the minimum necessary requirements.
◈ Automatic Logoff. As HIPAA requires the confidentiality of PHI, automatic logoff is an essential part of HIPAA. Automatic logoff locks an employee’s computer when left unattended for a pre-designated length of time. Automatic logoff prevents, intentional and unintentional, unauthorized access to PHI.
◈ Emergency Access. HIPAA also requires the availability of PHI. As such, it is imperative that organizations have access to data in the event of an emergency. To ensure uninterrupted access to PHI, data should be backed up frequently and stored on an offsite server.
User Authentication and Access Management.
HIPAA compliant software includes a means to authenticate and manage users. As previously mentioned, unique login credentials enable both. User authentication requires unique login credentials for each employee, however, for increased security, HIPAA software developers should enable multi-factor authentication (MFA). MFA utilizes multiple login credentials (i.e. a username and password in combination with security questions, one-time PIN, biometrics, etc.) to ensure that users are who they appear to be. Access management requires access to PHI to be revoked for employees that no longer need access, or for user access to be adjusted if an employee changes job roles.
Audit Controls.
To prevent and easily detect unauthorized access to PHI, it is essential to implement audit controls. Audit controls track access to PHI based on users’ unique login credentials. By tracking access to data, normal access patterns to data are established for each user. Tracking access to data ensures that unauthorized access to data can be quickly detected.
Encryption.
To maintain both the confidentiality and integrity of PHI, the data must be secured. Encryption masks sensitive data so that it can only be accessed by authorized users possessing a decryption key.
Transmission Security.
To further increase data security, HIPAA software development requires transmission security to be implemented. To prevent unauthorized access to data, products should implement SSL and TLS certificates when possible.
HIPAA Software Development: Business Associate Agreements
As with any other business associate, healthcare software developers must be willing to sign a business associate agreement (BAA) to work with healthcare clients. A BAA mandates the protections that the business associate is required to have in place. In addition, a BAA requires each signing party to be HIPAA compliant, and states that each party is responsible for maintaining their own compliance.






