How to Conduct a Security Risk Assessment
Conducting a security risk assessment is an important part of making sure that your data is secure. In the healthcare space, conducting a risk assessment is also a key component of HIPAA compliance. As risk assessment season is just around the corner, how to conduct a security risk assessment is discussed.
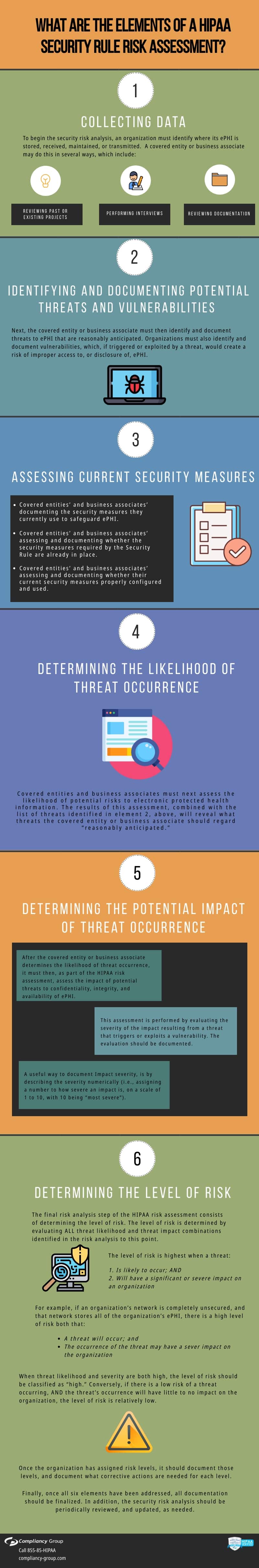
How to Conduct a Security Risk Assessment: Step 1
The first step to conduct a security risk assessment is “Collecting Data.” The collecting data aspect of conducting a security risk assessment refers to your organization identifying where your electronic protected health information (ePHI) is stored, created, maintained, received, or transmitted. This can be accomplished by reviewing past or present projects, interviewing staff members, or reviewing documentation.
How to Conduct a Security Risk Assessment: Step 2
The second step to conduct a security risk assessment is “Identifying and Documenting Potential Threats and Vulnerabilities.” To ensure that you are adequately securing ePHI, you must identify any reasonably anticipated threats to ePHI, document the threats, and address identified threats with remediation efforts.
How to Conduct a Security Risk Assessment: Step 3
The third step to conduct a security risk assessment is “Assessing Current Security Measures.” This step requires you to assess your current ePHI safeguards.
To assess your security measures, you may be asked:
- “Have you assessed and documented the security measures you use to protect ePHI?”
- “Are the security measures required by the HIPAA Security Rule already in place?”
- “Are your current security measures properly configured and used?”
How to Conduct a Security Risk Assessment: Step 4
The fourth step to conduct a security risk assessment is “Determining the Likelihood of Threat Occurrence.” To determine the likelihood of a threat occurrence, you may ask “Is there a likelihood of potential risks to ePHI, based on the threats you have identified?” If the answer to that question is “yes,” the organization should document the likelihood of a particular risk associated with a particular threat.
How to Conduct a Security Risk Assessment: Step 5
The fifth step to conduct a security risk assessment is “Determining the Potential Impact of Threat Occurrence.” To minimize damage in the event of an incident, it is important to determine the impact a threat would have to your organization. When you anticipate the damage an incident can have to your organization, you are better prepared should one occur.
How to Conduct a Security Risk Assessment: Step 6
The sixth step to conduct a security risk assessment is “Determining the Level of Risk.” In this last step, you evaluate your level of risk through the identified combinations of threat likelihood and threat impact. If it is determined that both threat likelihood and threat severity are high, the level of risk would be classified as “high.” Threat levels must be documented, and remediation plans must be created to address identified vulnerabilities.
How Often Should a Security Risk Assessment Be Conducted
HIPAA standards require healthcare organizations to conduct a security risk assessment annually. By doing so, any changes to the way you store, create, maintain, receive, or transmit ePHI can be accounted for. Thus ensuring your ePHI remains secure, and you maintain your HIPAA compliance.






