What Information is Protected Under HIPAA Law?
What information is protected under HIPAA law? HIPAA law requires organizations working with protected health information (PHI) to ensure its confidentiality, integrity, and availability.
What Information is Protected Under HIPAA Law?
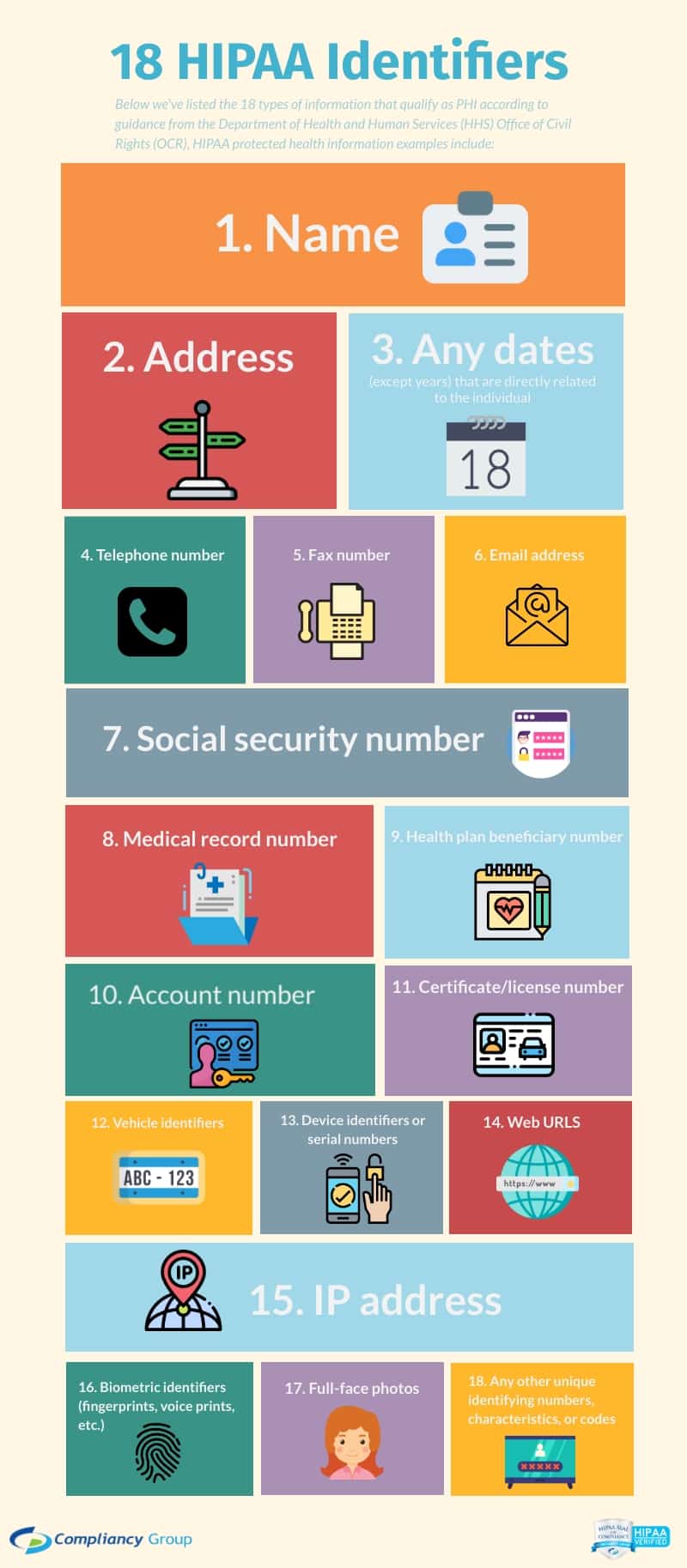
What information is protected under HIPAA law? The answer to this question is protected health information. PHI is any individually identifying health information that communicates the past, present, or future health of a patient. The Department of Health and Human Services (HHS) categorizes PHI into 18 identifiers.
- Patient names
- Geographical elements (such as a street address, city, county, or zip code)
- Dates related to the health or identity of individuals (including birthdates, date of admission, date of discharge, date of death, or exact age of a patient older than 89)
- Telephone numbers
- Fax numbers
- Email addresses
- Social security numbers
- Medical record numbers
- Health insurance beneficiary numbers
- Account numbers
- Certificate/license numbers
- Vehicle identifiers
- Device attributes or serial numbers
- Digital identifiers, such as website URLs
- IP addresses
- Biometric elements, including finger, retinal, and voiceprints
- Full face photographic images
- Other identifying numbers or codes
Securing Protected Health Information
The HIPAA Security Rule mandates that protected health information (PHI) is secured in the form of administrative, physical, and technical safeguards. As part of the HIPAA Security Rule, organizations must have standards for the confidentiality, integrity, and availability of PHI.
- Confidentiality: PHI may not be disclosed without prior patient authorization
- Integrity: PHI that is transmitted or maintained must only be accessed by those who need access to perform job functions
- Availability: organizations and patients must be able to easily access PHI
HIPAA Safeguards
- Administrative: Include creating policies and procedures dictating the proper use and disclosure of PHI. PHI should only be used or disclosed to complete a specific job function, known as the minimum necessary standard. To ensure that this standard is met, employees must be trained annually on their organization’s policies and procedures, as well as HIPAA standards.
- Physical: Include securing areas that contain PHI. Physical safeguards may include installing alarm systems, locks on doors and cabinets storing patient files, CCTV cameras, etc.
- Technical: Include securing devices that have access to electronic protected health information (ePHI). ePHI is protected health information in electronic form. Technical safeguards may include encryption, firewalls, antivirus, multi-factor authentication (MFA), etc.
Implementing an Effective HIPAA Compliance Program
To ensure that PHI is adequately safeguarded, it is important to implement an effective HIPAA compliance program.
- Self-assessments: To measure your organization’s compliance with HIPAA, you must complete annual self-audits. There are six required audits for HIPAA covered entities (CEs), and five for business associates (BAs).
- IT Risk Analysis Questionnaire: is meant to create a standard device installation and setup process across an entire organization.
- Security Standards: ensures that an organization’s security policies are in line with HIPAA requirements.
- HITECH Subtitle D: ensures that an organization has proper documentation and protocols in relation to Breach Notification.
- Asset and Device: is an itemized inventory of devices that contain ePHI. The device and asset list includes who uses the device and how an organization is protecting the device.
- Physical Site: each physical location must be assessed to determine if there are measures protecting PHI such as locks or alarm systems.
- Privacy Assessment (not required for BAs): assesses an organization’s privacy policies to ensure that PHI is used and disclosed in accordance with HIPAA.
- Gap Identification and Remediation: Completing self-audits allows you to identify areas in which your safeguards are lacking. Gap identification enables you to create remediation plans to address deficiencies.
- Policies and Procedures: As stated above, policies and procedures dictate the proper uses and disclosures of PHI. Policies and procedures must be customized for your organization to apply directly to your business processes, and must be reviewed annually to account for any changes in business operations. Failure to customize policies and procedures leaves your organization vulnerable as PHI may not be fully secured.
- Employee Training and Tracking: Also mentioned above, employee’s must be trained annually on your organization’s policies and procedures, as well as HIPAA standards. Employees must legally attest that they have read and understand the material that they were trained on. The ability to track employees’ training ensures that all employees are trained in a timely manner.
- Business Associate Management: Organizations working with protected health information are required to vet their business associates. Vetting BAs ensures that they are protecting the PHI that they create, receive, transmit, maintain, or store on your behalf. You can vet your BAs by sending them a vendor questionnaire. Similar to self-audits, vendor questionnaires assess the gaps in the business associate’s safeguards. To work with the BA, the vendor must agree to address identified gaps with remediation efforts. If the BA is unwilling to implement remediation plans, you should choose another vendor to work with. Additionally, they must be willing to sign a business associate agreement (BAA). A BAA is a legal document that dictates the safeguards the BA must have in place. It also limits the liability of each signing party as it requires each party to manage their own HIPAA compliance.
- Incident Management: If your organization is the victim of a healthcare breach, you must report the breach. If the breach affects less than 500 patients, you are required to report the incident within 60 days from the end of the calendar year to affected patients and the Department of Health and Human Services (HHS). If the breach affects 500 or more patients, you must report it within 60 days of discovery to affected patients, the HHS, and the media.