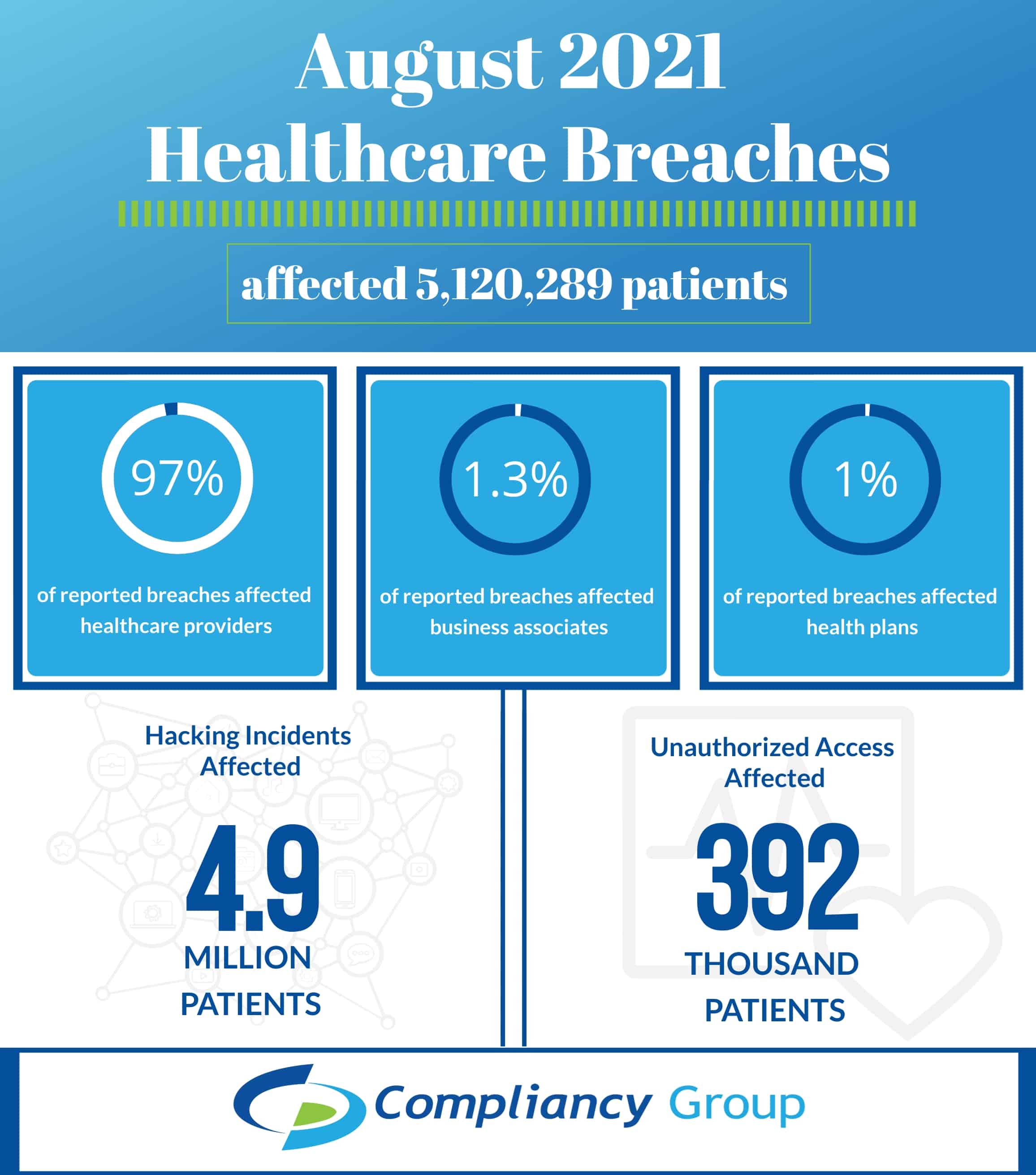
The Department of Health and Human Services (HHS) Office for Civil Rights (OCR) publicly posts breaches affecting 500 or more patients to their online breach portal, known as the “HIPAA Wall of Shame.” In August 2021, there were 38 breaches posted on the portal, affecting 5,120,289 patients. August 2021 healthcare breaches predominantly consisted of hacking incidents affecting healthcare providers, with 4,656,453 patients affected by hacking incidents targeting healthcare providers.
Overall, August 2021 healthcare breaches:
- Affected 30 healthcare providers, representing 97.63% of total patients affected
- Affected 4 business associates, representing 1.29% of total patients affected
- Affected 4 health plans, representing 1.07% of total patients affected
August 2021 Hacking Incidents Affected 4.7 Million Patients
Hacking incidents are generally the leading cause behind healthcare breaches, and August was no different. In fact, 31 of the 38 August reported breaches were due to hacking incidents, representing 92.33 % of patients affected by August breaches (4,727,350 patients).
- 25 healthcare providers were targeted by hacking incidents, affecting 4,656,453 patients, representing 98.5% of patients affected by hacking
- 4 business associates were targeted by hacking incidents, affecting 66,201 patients, representing 1.40% of patients affected by hacking
- 2 health plans were targeted by hacking incidents, affecting 4,696 patients, representing 0.10% of patients affected by hacking
Hackers infiltrated these healthcare organizations through two methods, network server hacks and email hacks (phishing).
There were:
- 18 network server hacking incidents, affecting 4,385,486 patients, representing 92.77% of patients affected by hacking
- 13 email hacking incidents, affecting 341,864 patients, representing 7.23% of patients affected by hacking
How HIPAA Compliance Prevents Hacking
Hacking should be a concern for any business, but especially those working in healthcare. Hackers often target healthcare organizations to gain access to the sensitive information held on patients (protected health information). While hacking incidents seem to be unavoidable, there are certain ways in which you can better prepare your organization against hacking.
Conduct an Annual Security Risk Assessment and Implement Remediation Plans
As part of HIPAA requirements, organizations working with patient information must conduct an annual security risk assessment (SRA). SRAs enable healthcare organizations to better protect themselves against hacking incidents as they assess the organization’s security practices to identify risks and vulnerabilities to sensitive data, such as PHI. To be HIPAA compliant and bolster cybersecurity, it is important to implement remediation plans to address deficiencies identified by conducting your SRA.
Security Policies and Procedures
HIPAA security policies and procedures dictate minimum measures that organizations must take to protect electronic protected health information (ePHI). These measures include encryption, user authentication, access controls and audit logs, all of which make it more difficult for a hacker to infiltrate your organization’s systems.
Employee Cybersecurity Awareness Training
Employee error is one of the leading causes behind breaches. Hackers often target employees through phishing emails by posing as a trusted entity, meant to trick employees into clicking a malicious link or divulging login credentials. As a major risk factor to your organization’s security, it is important to regularly train employees (HIPAA requires annual training) on cybersecurity best practices, and particularly, how to recognize phishing attempts.
Business Associate Agreements
Healthcare providers are often targeted by hackers through their business associates, as many fail to adequately safeguard PHI. This is why the HHS requires business associates to be HIPAA compliant and enter into business associate agreements (BAAs) with their healthcare clients. BAAs are legal contracts that require each signing party to be HIPAA compliant, and be responsible for maintaining their compliance.
392,939 Patients Affected by Incidents of Unauthorized Access or Disclosures
Incidents of unauthorized access or disclosure occur when PHI is accessed by an unauthorized party, or accessed or disclosed by an authorized party without cause.
- 5 healthcare providers reported incidents of unauthorized access or disclosure, affecting 342,729 patients, representing 87.22% of patients affected by these types of incidents
- 2 health plans reported incidents of unauthorized access or disclosure, affecting 50,210 patients, representing 12.78% of patients affected by these types of incidents
These incidents of unauthorized access or disclosure occurred via email, network server, paper/films, and electronic medical records.
- 1 incident of unauthorized access or disclosure through network server, affecting 326,417 patients, representing 83.07% of patients affected by unauthorized access or disclosure
- 2 incidents of unauthorized access or disclosure through email, affecting 50,210 patients, representing 12.78% of patients affected by unauthorized access or disclosure
- 2 incidents of unauthorized access or disclosure through electronic medical records, affecting 10,885 patients, representing 2.77% of patients affected by unauthorized access or disclosure
- 2 incidents of unauthorized access or disclosure through paper/films, affecting 5,427 patients, representing 1.38% of patients affected by unauthorized access or disclosure
How HIPAA Prevents Unauthorized Access or Disclosures
Unauthorized access or disclosure of PHI mostly occurs accidentally, but can occur when employees that are authorized to access PHI do so without cause.
Privacy Policies and Procedures
Privacy policies dictate the proper uses and disclosures of PHI, requiring healthcare organizations and their employees to adhere to the minimum necessary standard. This standard dictates that PHI access and disclosure should be limited to only what is necessary to perform a job function.
Employee HIPAA Training
To ensure that employees are aware of HIPAA obligations, they must be trained annually on HIPAA standards. Employees must also be trained on their organization’s HIPAA policies and procedures, and legally attest that they agree to adhere to them.
2021 August OCR Wall of Shame
The following organizations were listed on the OCR wall of shame, having experienced an August 2021 healthcare breach affecting 500 or more patients.
Healthcare Providers and Hacking
- Ijaola, LLC d/b/a Mercy Grace Private Practice: 4,450 patients affected
- Queen Creek Medical Center d/b/a Desert Wells Family Medicine: 35,000 patients affected
- Easterseals Delaware & Maryland’s Eastern Shore: 501 patients affected
- DuPage Medical Group, Ltd.: 655,384 patients affected
- CareATC, Inc.: 98,774 patients affected
- Beaumont Health: 1,568 patients affected
- Family Medical Center of Michigan: 21,988 patients affected
- LifeLong Medical Care: 115,448 patients affected
- The Wedge Medical Center: 29,000 patients affected
- CarePointe ENT: 48,742 patients affected
- Gregory P. Vannucci DDS: 26,144 patients affected
- Central Utah Clinic, P.C. dba Revere Health: 12,433 patients affected
- Nashua Regional Cancer Center dba Radiation Center of Greater Nashua : 520 patients affected
- Metro Infectious Disease Consultants: 171,740 patients affected
- Texoma Community Center: 24,030 patients affected
- Fairfax Medical Facilities, Inc.: 4,970 patients affected
- University Medical Center Southern Nevada: 1,300,000 patients affected
- North Country Healthcare: 3,550 patients affected
- Children’s Hospital of The King’s Daughters: 914 patients affected
- St. Joseph’s/Candler Health System, Inc.: 1,400,000 patients affected
- Electromed: 47,200 patients affected
- Wisconsin Institute of Urology S.C.: 4,819 patients affected
- UNM Health: 637,252 patients affected
- Vision for Hope: 1,344 patients affected
- Hospice of the Piedmont: 10,682 patients affected
Healthcare Providers and Unauthorized Access or Disclosures
- Denton County, Texas : 326,417 patients affected
- UTMP Surgical Oncology: 1,310 patients affected
- Alluma, Inc: 4,117 patients affected
- Frisco Fertility Center, PLLC dba Dallas IVF: 552 patients affected
- Long Island Jewish Forest Hills Hospital: 10,333 patients affected
Business Associates and Hacking
- Medical Business Management: 1,750 patients affected
- San Andreas Regional Center: 57,244 patients affected
- McCoy Consulting Services LLC: 5,500 patients affected
- Express MRI – Norcross, LLC: 1,707 patients affected
Health Plans and Hacking
- Nova Biomedical Corporation : 3,774 patients affected
- Waste Management Health and Welfare Benefits Plan: 922 patients affected
Health Plans and Unauthorized Access or Disclosures
- South Florida Community Care Network LLC d/b/a Community Care Plan: 48,344 patients affected
- Valley Physical Medicine & Rehabilitation: 1,866 patients affected