HIPAA in a Nutshell
The HIPAA regulations require healthcare organizations to follow a set of standards. However, these standards are written in a way which poses more questions than answers. What do you really need to do to be HIPAA compliant? To take the guesswork out of HIPAA, HIPAA in a nutshell is discussed below.
HIPAA in a Nutshell: The Three HIPAA Rules
Really, the HIPAA regulation can be broken down into three major components, the Privacy, Security, and Breach Notification Rules. These Rules are meant to ensure the confidentiality, integrity, and availability of protected health information.
HIPAA in a Nutshell: What is Protected Health Information?
Before we get into what each of the HIPAA Rules entails, it is important to understand what protected health information consists of. Protected health information (PHI) is any individually identifiable health information related to the past, present, or future provision of healthcare. The Department of Health and Human Services (HHS) classifies PHI into 18 identifiers.
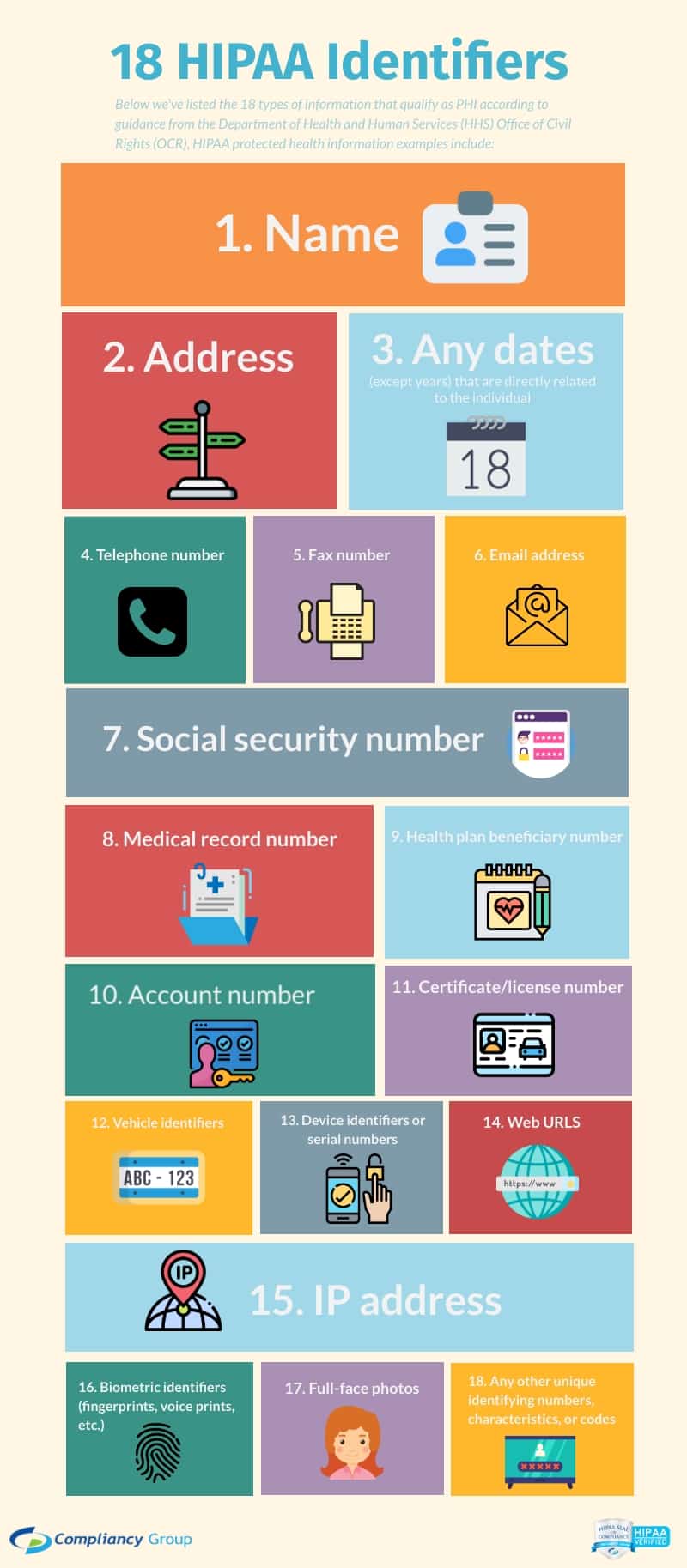
◈ Patient names
◈ Geographical elements
◈ Dates related to the health or identity of individuals
◈ Telephone numbers
◈ Fax numbers
◈ Email addresses
◈ Social Security numbers
◈ Medical record numbers
◈ Health insurance beneficiary numbers
◈ Account numbers
◈ Certificate/license numbers
◈ Vehicle identifiers
◈ Device attributes or serial numbers
◈ Digital identifiers, such as website URLs
◈ IP addresses
◈ Biometric elements, including finger, retinal, and voiceprints
◈ Full face photographic images
◈ Other identifying numbers or codes
HIPAA in a Nutshell: HIPAA Privacy Rule
As a healthcare organization, by the nature of your work, you most likely use and disclose PHI. It is permitted to use and disclose PHI (without patient authorization) for the purposes of treatment, payment, and healthcare operations. As part of the HIPAA Privacy Rule, healthcare workers should only have access to the PHI that they need to perform their job functions, known as the minimum necessary standard. As such, to ensure HIPAA compliance, healthcare organizations are required to issue unique login credentials for each employee, enabling them to designate different levels of access to PHI based on the employee’s job role. Additionally, access to PHI must be tracked and documented with audit logs to ensure adherence to the minimum necessary standard, and minimize the risk of insider breaches.
The HIPAA Privacy Rule also establishes patient rights in regards to their PHI. This includes the HIPAA right of access which requires healthcare organizations to provide patients access to their medical records within 30 days of the request. It also prohibits organizations from overcharging patients for access to their medical records. The HIPAA right of access has become more prominent as of late, as the HHS’ Office for Civil Rights (OCR) has issued nine right of access fines in 2020 so far.
So now that we have discussed the permitted uses and disclosures of PHI, and how you can control and monitor access to PHI, you may be wondering how you can protect PHI from unauthorized access. This is where the HIPAA Security Rule comes into play.
HIPAA in a Nutshell: HIPAA Security Rule
The HIPAA Security Rule requires you to:
◈ Ensure the confidentiality, integrity, and availability of all ePHI you create, receive, maintain, or transmit;
◈ Identify and protect against reasonably anticipated threats to the security or integrity of the information;
◈ Protect against impermissible uses or disclosures of ePHI that are reasonably anticipated; and
◈ Ensure compliance by their workforce.
This is accomplished by implementing administrative, technical, and physical safeguards to secure PHI.
Administrative. Administrative safeguards require you to conduct self-audits to identify gaps in your security measures, and to address those gaps with remediation efforts. This also requires you to have documented policies and procedures that dictate how your organization will follow the HIPAA Rules. To ensure a culture of compliance within your organization, employees must be trained annually on your organization’s policies and procedures, and HIPAA basics.
Technical. Technical safeguards ensure that your electronic protected health information (ePHI) – PHI stored electronically – is secure. This is accomplished through access controls (unique login credentials), audit controls (audit logs that track access to ePHI), integrity controls (policies and procedures), and transmission security (encryption).
Physical. Physical safeguards ensure the security of your physical location, and your paper PHI. This includes installing alarm systems, locking cabinets or rooms that store PHI, and installing CCTV cameras.
Since every organization has different security requirements, when implementing security measures, you must consider the following:
◈ Your size, complexity, and capabilities;
◈ Your technical hardware, and software infrastructure;
◈ The costs of security measures; and
◈ The likelihood and possible impact of the potential risk to ePHI.
HIPAA in a Nutshell: HIPAA Breach Notification
The HIPAA Breach Notification Rule requires organizations working with PHI to report breaches. Depending on the size of the breach, reporting requirements differ.
Breaches affecting 500 or more patients. These breaches must be reported within 60 days of discovery to the HHS OCR, affected patients, and the media. They are also publicly posted to the HHS’ OCR breach portal.
Breaches affecting less than 500 patients. These breaches must be reported within 60 days from the end of the calendar year (March 1) in which the breach was discovered. They must be reported to HHS OCR and affected patients.
HIPAA in a Nutshell: Implementing an Effective Compliance Program
Compliancy Group’s total HIPAA compliance solution covers the full extent of the HIPAA Privacy, Security, and Breach Notification Rules. What’s even better is that Compliancy Group’s clients don’t have to go through the compliance process on their own. Our expert Compliance CoachesTM guide clients through every step of the process with virtual meetings. Upon completion of our process, Coaches verify and validate your efforts, issuing you our Seal of ComplianceTM. The Seal is an industry-recognized third party verification tool that can be displayed on your website and email signature to prove your dedication to compliance. By working with Compliancy Group, you can become HIPAA compliant and earn your Seal in as little as 30 days!
Here is what our compliance solution offers:
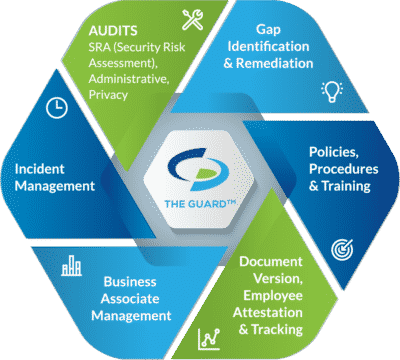
Self-audits. Covered entities are required to conduct six self-audits annually, while business associates and MSPs must complete five. Completing self-audits measures administrative, physical, and technical safeguards against HIPAA standards.
Gap Identification and Remediation. Upon completion of self-audits, gaps in your organization’s safeguards are identified. To be HIPAA compliant, gaps must be addressed with remediation plans. Remediation efforts close gaps so that your safeguards are adequately securing PHI.
Policies and Procedures. A major component of HIPAA is illustrating compliance through documentation. As such, you must have customized policies and procedures dictating how you adhere to the HIPAA Security, Privacy, and Breach Notifications Rules.
Employee Training. To ensure that employees properly use and disclose PHI, they must be trained annually. HIPAA training should include HIPAA basics, your organization’s policies and procedures, proper use of social media, and cybersecurity best practices.
Business Associate Management. Before working with a vendor, it is essential to assess their safeguards. Vendors (business associates) are required to be HIPAA compliant to work with healthcare clients. They must also be willing to sign a business associate agreement (BAA). A BAA must be signed before it is permitted to share PHI with the business associate. A BAA is a legal document that dictates the safeguards the business associate is required to have in place, it also requires each party to be responsible for maintaining their compliance.
Incident Response. If your organization experiences a breach, you have an obligation to report it. Additionally, employees must have a means to report breaches anonymously. Our HIPAA software allows this, while also allowing administrators to track reported incidents.




