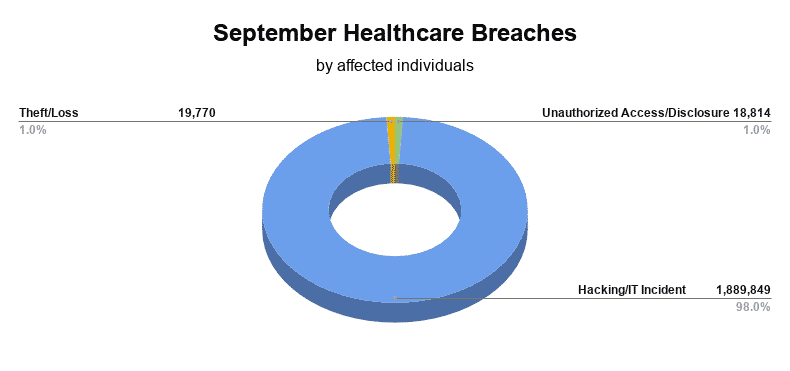
September healthcare breaches reported to the Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) affected 1,928,433 individuals. The majority of the 33 reported September healthcare breaches were the result of Hacking/IT Incidents, affecting 1,889,849 patients. Unauthorized Access/Disclosures affected 18,814, while Theft/Loss affected 19,770 patients.
Hacking/IT Incident
- Wood Ranch Medical: network server hack affecting 5,835
- Magellan Healthcare: email hack affecting 55,637
- National Imaging Associates: email hack affecting 589
- Paragon Health, P.C.: email hack affecting 4,674
- Bates Technical College: network server hack affecting 2,112
- Sweetser: email hack affecting 22,000
- Kilgore Vision Center: network server hack affecting 40,000
- Berry Family Services: network server hack affecting 1,751
- Premier Family Medical: network server hack affecting 320,000
- Shore Speciality Consultants Pulmonology Group: desktop computer and network server hack affecting 9,700
- East Central Indiana School Trust: email hack affecting 3,259
- Goshen Health: email hack affecting 9,160
- Cancer Treatment Centers of America (CTCA) at Southeastern Regional Medical Center: email hack affecting 3,290
- Kaiser Permanente: email hack affecting 990
- Sarrell Dental: network server hack affecting 391,472
- Pima County: email hack affecting 1,498
- CHI Health Orthopedics Clinic – Lakeside: network server hack affecting 48,000
- Choctaw Nation Health Service Authority: email hack affecting 500
- Beatitudes Campus: email hack affecting 514
- Women’s Care Florida, LLC: network server hack affecting 528,188
- Intramural Practice Plan – Medical Sciences Campus – University of Puerto Rico: network server hack affecting 439,753
Unauthorized Access/Disclosure
- Chirobody: unauthorized access of a desktop computer affecting 525
- Premier Gastroenterology Specialists: unauthorized access or disclosure of paper/films affecting 1,260
- Rocky Mountain Health Maintenance Organization, Inc.: unauthorized access or disclosure of paper/films affecting 1,835
- June E. Nylen Cancer Center: unauthorized access to email affecting 927
- Alive Hospice: unauthorized access or disclosure of paper/films affecting 533
- Health Care Services Corporation: unauthorized access or disclosure of paper/films affecting 998
- Rural Health Access Corporation dba Coalfield Health Center: unauthorized access to email affecting 874
- Little Rock Plastic Surgery, P.A.: unauthorized access to email account affecting 6,300
- Medico of South Carolina, Inc.: unauthorized access of network server affecting 6,489
Theft/Loss
- Prisma – Midlands: theft of paper/films affecting 2,770
- Simmons Family Chiropractic: theft of laptop or other portable electronic device affecting 2,000
- Perfect Teeth Yale, P.C.: loss of portable electronic device affecting 15,000
How to Protect Against Healthcare Breaches
Healthcare breaches can be costly and damaging to an organization’s reputation, as such it should be a top priority for any organization working in healthcare to secure patients’ sensitive information. Protected health information (PHI), when accessed by those with malintent, can be used to steal a person’s identity or commit financial fraud, making PHI extremely valuable.
The HHS recommends that organizations working with PHI implement the following ten cybersecurity practices:
- Email protection systems: refers to securing email communications; although not specifically mandated by HIPAA, emails should be encrypted to ensure secure communications. In addition, utilizing secure passwords and Multi-factor Authentication (MFA) will further secure communications.
- Endpoint protection systems: refers to the process of protecting a business network by securing the various endpoints connected to the network. An endpoint is a device that connects to an organization’s internal network such as a laptop, smartphone, tablet, or a server in a data center.
- Access management: controls which individuals can view certain information, delegating different levels of access based on an employee’s job role. HIPAA requires entities to access only the “minimum necessary” PHI to perform a job function. For example, someone working in the billing department doesn’t need access to patient medical records, just as nurses don’t need access to patient’s financial information.
- Data protection and loss prevention (DLP): ensures that only authorized users have access to sensitive data, and that data is not lost or misused. DLP software categorizes data to identify confidential information or information critical to business operations. Data loss prevention software is also able to detect security violations and provide remediation alerts.
- Asset management: refers to tracking and maintaining any device that stores or accesses electronic protected health information (ePHI). Organizations must compile a list of assets including who uses the device and what protections are in place to secure ePHI.
- Network management: refers to the process of securing an organization’s internal network. Network security includes access controls, audit controls, encryption, and data backup. Each employee should have unique login credentials to access their organization’s network, this enables audit controls. Audit controls keep a log of normal activity for each individual, enabling the quick detection of insider breaches. Encryption protects data if a network is accessed by an unauthorized individual, while data backup ensures that files are recovered if they are lost or stolen.
- Vulnerability management: refers to the process of managing network security by identifying possible risks in an organization’s network, and addressing those risks with remediation efforts. Network scanning, firewall logging, and penetration testing are means in which vulnerabilities can be identified. To address vulnerabilities, in many cases, software patches can be implemented, however, when patches are unavailable network access should be restricted for vulnerable devices.
- Incident response: organizations should develop an incident response plan to quickly identify and respond to breaches. The incident response plan should identify what to do when a breach is suspected, who to report breaches to, how to respond quickly, how to contain the breach, and how to recover from the breach. A tested incident response plan drastically reduces the costs associated with a breach.
- Medical device security: refers to the security measures in place for medical devices that connect to a network. Devices such as pacemakers, drug infusion pumps, and heart rate monitors, connect to a network, making them vulnerable to cyberattacks. Medical device security is up to the device manufacturer, however, access controls should be implemented to ensure that user activity can be easily tracked.
- Cybersecurity policies: are written policies surrounding an organization’s security controls and activities. Cybersecurity policies should be drafted with HIPAA requirements in mind. Organizations must ensure that technical, physical, and administrative safeguards are incorporated into their cybersecurity policies.









