What is a HIPAA Risk Assessment Checklist?
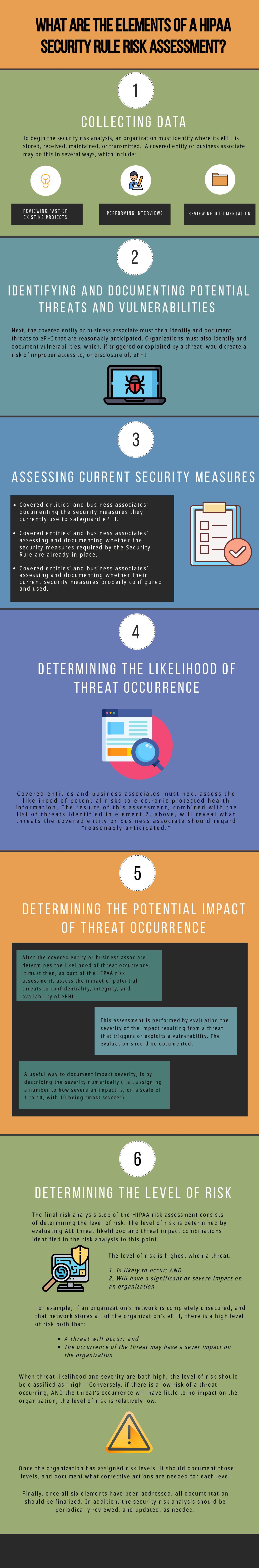
The HIPAA Security Rule requires covered entities and business associates to implement a series of safeguards. These safeguards are designed to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI). In order to properly identify what safeguards are needed, and how to implement them, an organization must perform a security risk assessment (sometimes called a security risk analysis). The HIPAA risk assessment consists of six components. The topic of how to develop a HIPAA risk assessment checklist is discussed below.
What is a HIPAA Risk Assessment Checklist? The Overall Goal
A security risk analysis is required by 45 CFR 164.308. The purpose of a risk assessment checklist is to cover the basic implementation requirements of the assessment.
The HIPAA risk assessment checklist should be developed from the requirements contained in the 6 components.
Component one of the risk assessment is “collecting data.” The HIPAA risk assessment checklist should contain “yes or no” questions regarding this component, as well as components two through five. A “yes: response means that the organization has performed what is required by the risk assessment, while a “no” response means the organization has not. The HIPAA risk assessment checklist question for component one should be, ”Have you identified where ePHI is created, stored, received, maintained, or transmitted?”
Component two of the risk assessment is “Identifying and Documenting Potential Threats and Vulnerabilities.” These are threats to ePHI that are reasonably anticipated. The HIPAA risk assessment question for component two should be something along the lines of, “Have you identified and documented threats to ePHI that are reasonably anticipated?” Component two also requires an organization to identify and document vulnerabilities, which, if triggered or exploited by a threat, would create a risk of improper access to, or disclosure of, ePHI.” The HIPAA risk assessment checklist should therefore contain a question that asks, “Have you identified and documented vulnerabilities that can be exploited by a threat, and, if this exploitation occurs, would there be a risk of improper access or disclosure to ePHI?”
Component three requires an organization to assess the strength of its current security measures. Checklist questions for this component should ask:
- “Have you assessed and documented the security measures you use to protect ePHI?”
- “Are the security measures required by the HIPAA Security Rule already in place?”
- “Are your current security measures properly configured and used?”
Component four of the security risk analysis requires an organization to determine the likelihood of threat occurrence. The HIPAA risk assessment checklist questions for component four should ask, “Is there a likelihood of potential risks to ePHI, based on the threats you have identified?” If the answer to that question is “yes,” the organization should document the likelihood of a particular risk associated with a particular threat. For example, there is a risk that there will be a data breach if a hacker can install malware. In this case, the organization would need to determine how likely it is that the threat of malware would put ePHI at risk.
Component five requires an organization to determine the potential impact on the organization if a threat materializes. If, for example, a malware attack is carried out, what is the potential impact? Will internal business operations be affected? Will client or patient data be compromised? The HIPAA risk assessment checklist question for component five should ask, “If threat X triggers or exploits a vulnerability, would the impact be severe? Moderate? Low?” “X” represents the potential threats identified in component two. There may be a number of potential threats, so this HIPAA risk assessment checklist question may consist of more than one question. For example, the HIPAA risk assessment checklist can have one question that asks, “If malware exploits a vulnerability, would the impact be severe?” The checklist can have another question that asks, “If a trojan or adware exploits a vulnerability, would the impact be severe?”
In component six, the organization determines the level of risk, based on all of the threat likelihood and threat impact combinations identified so far.
The level of risk is highest when a threat 1) is likely to occur; AND 2) will have a significant or severe impact on an organization. For example, if a network is completely unsecured, and that network stores large amounts of ePHI, two things are likely to happen: A threat will occur, and its occurrence can severely impact operations. When threat likelihood and severity are both high, the level of risk should be classified as “high.” The HIPAA risk assessment checklist questions for component six should ask, “What is the level of risk for the following combination: the likelihood of threat X occurring, and the impact that occurrence will have?” If you have already determined the likelihood of both impact and occurrence as high, the answer to the HIPAA risk assessment checklist question should be “high level of risk.”
Do You Need Help with Your HIPAA Risk Assessment?
Compliancy Group offers clients a full HIPAA compliance program, including a HIPAA risk assessment, and all other required self-audits that identify your compliance gaps. Our Compliance Coaches™ assess your gaps, creating remediation plans to bring your safeguards up to HIPAA standards. Find out more about our HIPAA risk assessment, and how we can help you Achieve, Illustrate, and Maintain™ your compliance.



