How to Get HIPAA Certification in India

As a software developer in India, you may develop software for healthcare organizations. When providing healthcare organizations with software, you likely have contact with patient’s protected health information (PHI), which would make you a business associate, needing to be HIPAA compliant. How to get HIPAA certification in India is discussed below. Want help getting compliant? Click here.
HIPAA in India: How to Get HIPAA Certification in India
Although many companies claim to offer a HIPAA certification, the Department of Health and Human Services (HHS) does not recognize HIPAA certifications. So really, how to get HIPAA certification in India, comes down to implementing an effective compliance program, and having the documentation to prove that your HIPAA compliance program is sufficient to meet HHS standards.
Now that we have established that there is no such thing as a HIPAA certification, therefore no such thing as HIPAA certification India, let’s discuss how to implement an effective HIPAA compliance program.
HIPAA in India: Developing a HIPAA Compliance Program
HIPAA in India applies to businesses that work with companies that create, receive, transmit, store, or maintain protected health information (HIPAA business associates and covered entities). Protected health information (PHI) is any “individually identifiable health information” that HIPAA business associates or covered entities use to perform their job function (classified into 18 identifiers by the HHS).
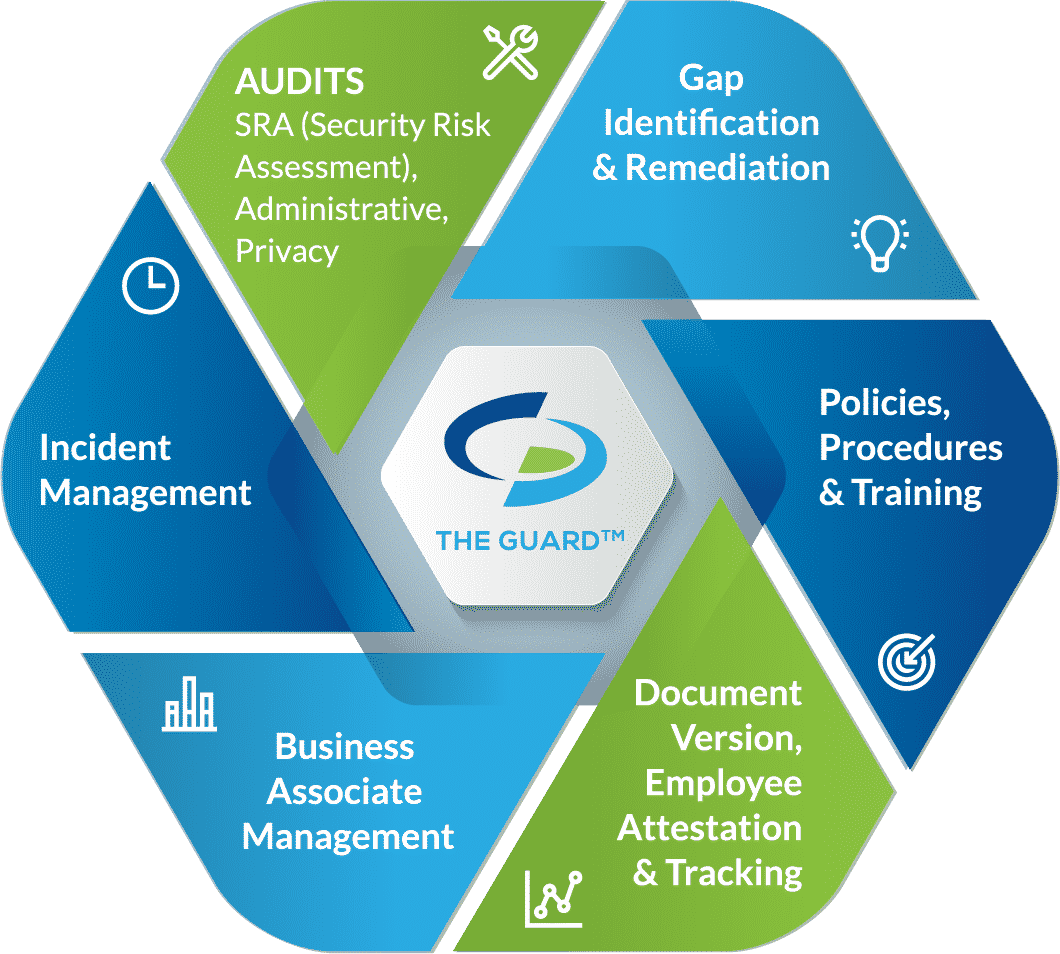
To ensure that you are adequately safeguarding PHI, you must implement an effective HIPAA compliance program.
- Self-audits. As a HIPAA business associate, the HHS requires you conduct five self-audits annually. These audits assess the administrative, physical, and technical safeguards that you have in place securing PHI.
- Gap identification and remediation. By conducting your self-audits, gaps in your safeguards are identified. To be HIPAA compliant, you must address your gaps with remediation efforts. Remediation efforts are meant to bring your administrative, physical, and technical safeguards up to HIPAA standards.
- Policies and procedures. Policies and procedures dictate the proper uses and disclosures of PHI by your organization. They also create a framework for how your organization adheres to the requirements of the HIPAA Security, Privacy, and Breach Notification Rules.
- Employee training. To ensure that your employees are aware of their HIPAA responsibilities, and that they adhere to your organization’s policies and procedures, you must train any employee that may come into contact with PHI. Employee training must be conducted annually and should include HIPAA basics, your organization’s policies and procedures, cybersecurity, and the proper use of social media.
- Business associate management. As a software developer, you likely work with other HIPAA business associates (such as your hosting provider, email provider, or other vendors that have access to your PHI data). Any entity that creates, receives, transmits, stores, or maintains PHI on your behalf must also be HIPAA compliant. As such, before sharing any PHI with another organization, you must vet them with a vendor questionnaire and sign a HIPAA business associate agreement (BAA). A vendor questionnaire assesses the vendor’s safeguards to ensure that they are in line with HIPAA standards. A BAA is a legal document that mandates that your vendors (business associates) have safeguards in place to secure the PHI you share with them. A BAA also requires both signing parties to be responsible for maintaining their HIPAA compliance.
- Incident management. If you were to experience a breach affecting PHI, you are required to report the incident. Incident management enables you to report breaches in a timely manner, give your employees means to report breaches anonymously, and track reported incidents.