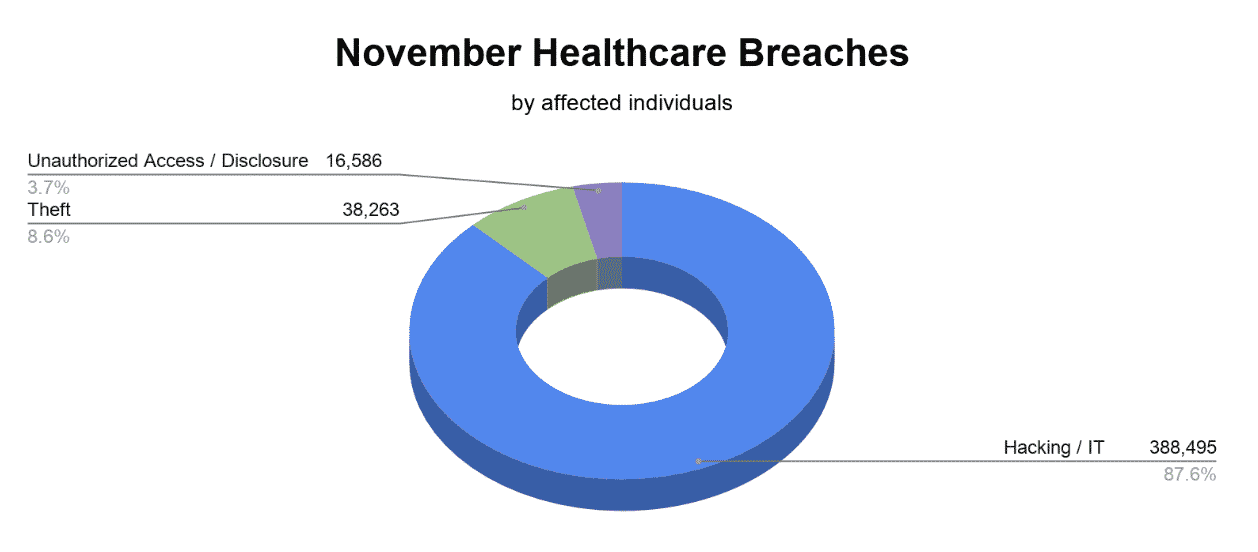
Healthcare breaches reported to the Department of Health and Human Services’ (HHS) Office for Civil Rights (OCR) in November affected 443,344 patients. There were a total of 26 November healthcare breaches including 15 hacking / IT incidents, 7 incidents of unauthorized access / disclosure of protected health information (PHI), and 4 incidents due to theft.
Hacking / IT Incidents Causing November Healthcare Breaches
November healthcare breaches were predominantly caused by hacking / IT incidents, with 87.6% of total November healthcare breaches related to this type of incident, affecting 388,495 patients.
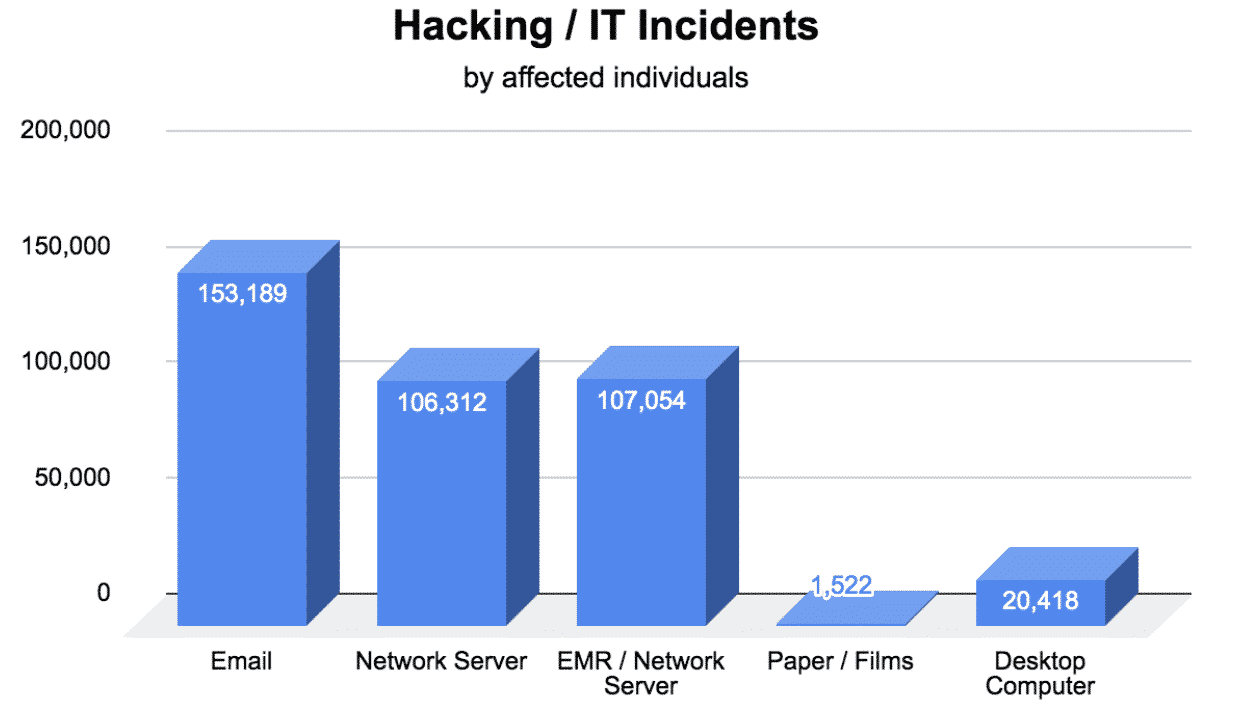
- Email Hacks Affected 153,189 Patients
-
- Penn-Mar Human Services: affected 536 patients
- Human Services, Inc.: affected 1,559 patients
- Choice Cancer Care: affected 14,673 patients
- Gateway Health Plan LP: affected 753 patients
- Solara Medical Supplies, LLC: affected 114,007 patients
- Select Health Network: affected 3,582 patients
- University of North Carolina at Chapel Hill School of Medicine: affected 3,716 patients
- Starling Physicians, P.C.: affected 977 patients
- Arizona Dental Insurance Services, Inc. d.b.a. Delta Dental of Arizona: affected 12,886 patients
- Outreach Health Services: affected 500 patients
- Network Server Hacks Affected 106,312 Patients
-
- Southeastern Minnesota Oral & Maxillofacial Surgery: affected 80,000 patients
- The Brooklyn Hospital Center: affected 26,312 patients
- Electronic Medical Record (EMR) / Network Server Hack Affected 107,054 Patients
-
- Saint Francis Medical Center: affected 107,054 patients
- Paper / Films Hack Affected 1,522 Patients
-
- Ronald E. Rosenbaum DMD, PA: affected 1,522 patients
- Desktop Computer Hack Affected 20,418 Patients
-
- Utah Valley Eye Center: affected 20,418 patients
Preventing Healthcare Hacking Incidents
Healthcare hacking incidents are occurring more frequently than ever before. As such, any organization working with protected health information (PHI) must be diligent in their efforts to secure PHI. Implementing the technical safeguards recommended by the HHS is the best way to prevent healthcare hacking incidents.
- Encryption: converts sensitive data into a format that is unreadable without a decryption key.
- Data Backup: stores data in an offsite server ensuring that if PHI is stolen or maliciously encrypted, it can be restored quickly.
- Firewalls: prevents unauthorized access to an organization’s network server.
- Employee Training: ensures that employees can recognize phishing attempts. A phishing attempt occurs when hackers disguise themselves as a trusted individual, prompting them to click on a malicious link, allowing hackers access to their system.
Unauthorized Access / Disclosure of PHI Causing November Healthcare Breaches
The unauthorized access or disclosure of protected health information (PHI) represented 3.7% of the total healthcare breaches in November, affecting 16,586 patients.
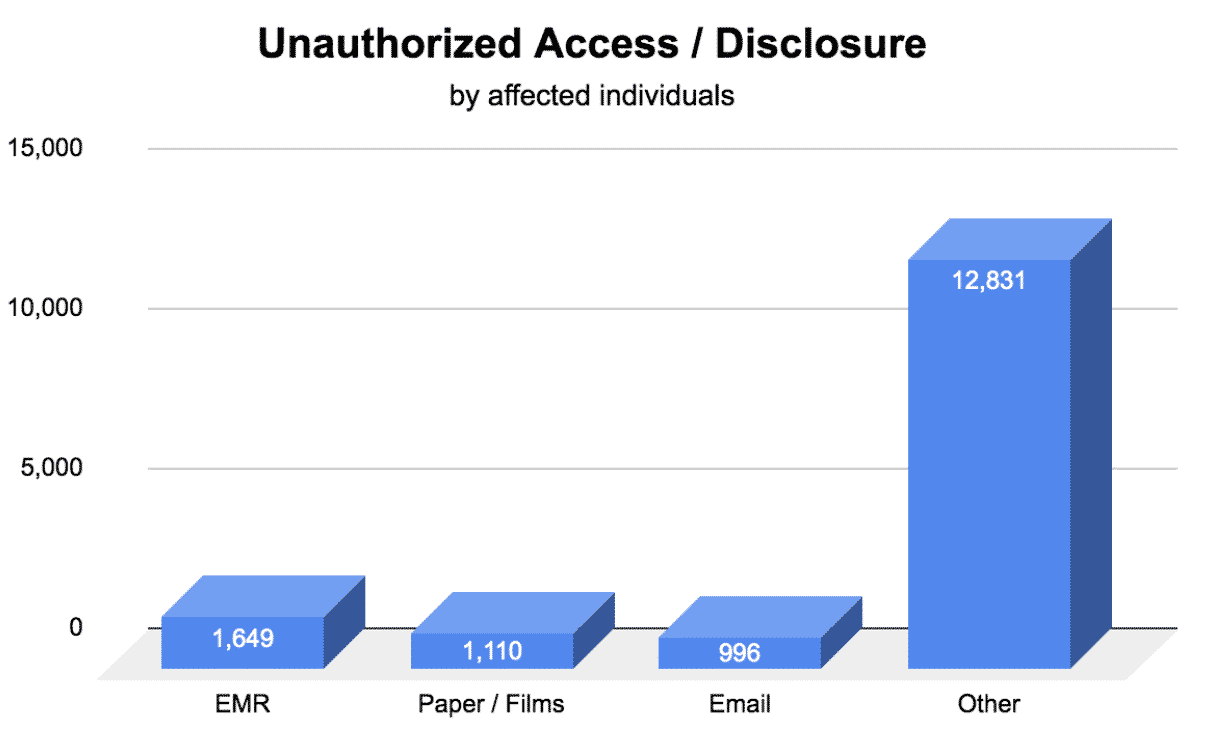
- Electronic Medical Record Unauthorized Access Affected 1,649 Patients
-
- Nebraska Medicine: affected 1,149 patients
- Medical Park Family Care, Inc.: affected 500 patients
- Paper / Films Unauthorized Access Affected 1,110 Patients
-
- VA St. Louis Health Care System: affected 595 patients
- Kaiser Foundation Health Plan (Kaiser Permanente: affected 515 patients
- Email Unauthorized Access Affected 996 Patients
-
- Ascension Borgess Hospital: affected 996 patients
- Other Unauthorized Access / Disclosure Affected 12,831 Patients
-
- Main Street Clinical Associates: affected 3,031 patients
- Aegis Medical Group: affected 9,800 patients
Preventing Unauthorized Access /Disclosure of PHI
The Health Insurance Portability and Accountability Act (HIPAA) requires PHI to be accessed in accordance with the “minimum necessary” standard. This means that access to PHI should be limited to only the information required to perform a job function.
- Access Controls: requires employees to have unique login credentials to access PHI. This enables administrators to designate different levels of access to PHI based on an employee’s job role.
- Audit Controls: requires administrators to keep a log of access to PHI. This allows for normal access patterns to be established to ensure that employees are not accessing PHI excessively. Audit controls prevents insider breaches from occurring and allows administrators to easily identify possible threats.
- Policies and Procedures: establishes permitted use and disclosure of PHI.
- Employee Training: must be conducted annually. Employees are required to be trained on an organization’s policies and procedures as well as HIPAA requirements. This ensures that all employees are aware of how PHI is permitted to be used and disclosed.
Theft Causing November Healthcare Breaches
The theft of devices containing PHI represented 8.6% of the total healthcare breaches in November, affecting 38,263 patients.
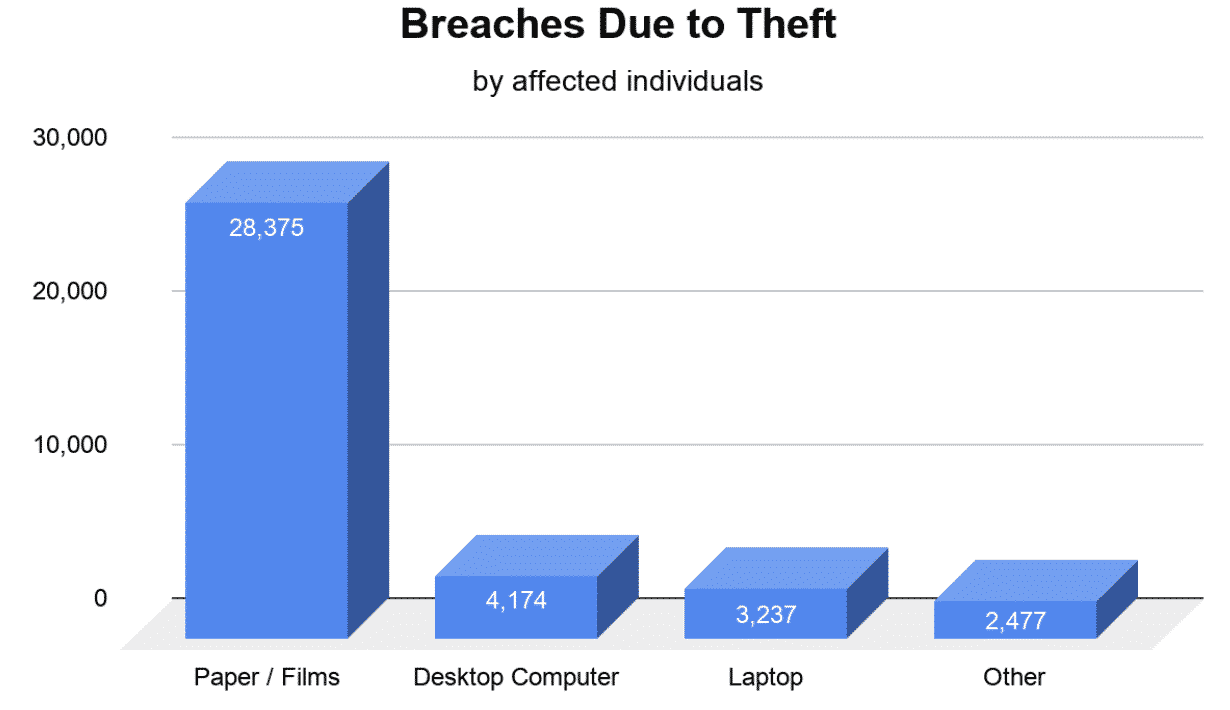
- Paper / Films Theft Affected 28,375 Patients
-
- Elizabeth Family Health: affected 28,375 patients
- Desktop Computer Theft Affected 4,174 Patients
-
- Evergreen Psychological Services: affected 4,174 patients
- Laptop Theft Affected 3,237 Patients
-
- Washington University School of Medicine: affected 3,237 patients
- Other Portable Electronic Device Theft Affected 2,477
-
- La Clinica de La Raza, Inc.: affected 2,477 patients
Preventing Theft of Devices Containing PHI
Loss or theft of devices containing PHI has the potential to expose thousands of patients. Although in many cases these incidents cannot be prevented, there are ways to limit exposure.
- Encryption: any device leaving an organization’s physical site should be encrypted. Encryption prevents sensitive data from being viewed by unauthorized individuals by converting the data into an unreadable format that is only accessible with a decryption key.
- Policies and Procedures: should be created around the use of unencrypted devices. Devices that lack encryption should not be permitted to be removed from an organization’s physical site, that includes laptops, tablets, mobile devices, thumb drives, or external hard drives.
- Employee Training: ensures that employees are aware of an organization’s policies and procedures surrounding the removal of devices containing PHI.








